Hi,
does this still work the same in 3.8.1? I’ve set up privacyIDEA with AD/LDAP and TOTP and that works fine with FortiGate VPN.
I need to restrict users per AD groups, and using multiple VPN tunnels, so I’m adding a group name beside the RADIUS server in Fortigate.
I added relevant section for Fortinet-Group-Name. For testing I didn’t even bother with regex yet but assigned a value directly to the AVP/VSA Fortinet-Group-Name.
[Mapping]
Fortinet-Group-Name = VPN_ADgroup (this is just for testing, I will use regex as there are more than one group/tunnel).
However, when using httpie on /validate/check it seems rlm_perl.ini is not processed, radiusd.log (set to debug) shows NO activity (just sits there, nothing comes up in the log), and there are no additional attributes in the response (as is in the post above from wwalker).
HTTP/1.1 200 OK
Cache-Control: no-cache
Connection: Keep-Alive
Content-Length: 1082
Content-Type: application/json
Date: Thu, 13 Jul 2023 11:12:19 GMT
Keep-Alive: timeout=5, max=100
Server: Apache
{
"detail": {
"message": "matching 1 tokens",
"otplen": 6,
"serial": "TOTPXXXXXXX",
"threadid": 140563761612544,
"type": "totp",
"user": {
"email": "",
"givenname": "",
"memberOf": [
"CN=VPNgroupname,CN=Users,DC=somedomain,DC=com",
"CN=Domain Users,CN=Users,DC=somedomain,DC=com"
],
"mobile": "",
"password": "",
"surname": "",
"username": "test2"
}
},
"id": 2,
"jsonrpc": "2.0",
"result": {
"authentication": "ACCEPT",
"status": true,
"value": true
},
"signature": "rsa_sha256.....
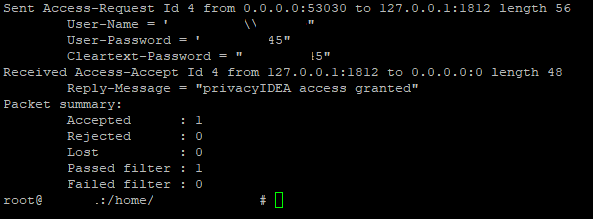
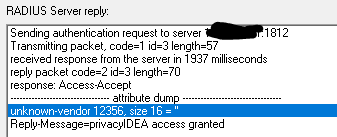
If I try to connect using VPN client and the request is sent by the firewall to the privacyIDEA then I do see radiusd.log processing, and I can see it assigns (at least it says it did) the attribute value. However, I’ve no idea what does it send back as I can’t see the response. And the VPN connection is not created with “wrong credentials” message from the VPN.
So, from the radiusd.log:
Thu Jul 13 12:28:43 2023 : Info: rlm_perl: +++ Map: Fortinet-Group-Name -> VPNADgroup
Thu Jul 13 12:28:43 2023 : Info: rlm_perl: return RLM_MODULE_OK
Thu Jul 13 12:28:43 2023 : Auth: (10) Login OK: [test2] (from client fw_iface port 0 some_IP)
VPN connection is still dropped even though VPNADgroup matches verbatim to what’s put in the FortiGate VPN’s user group using RADIUS and group.
What am I missing here? When requesting from the firewall it appears rlm_perl.ini is processed, but the firewall still dumps the connection with “wrong credentials” (although they’re correct, the AVP/VSA name and value are correct). It works without adding group with radius.
When I check /validate/check with httpie it seems rlm_perl.ini is not processes and I don’t see additional radius attributes in it - I’d love to be able to see what is sent back to the firewall so I can troubleshoot.
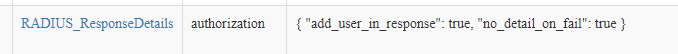
I did add the policy to include user details, mutlivalue memberOf and I can see those in the response to httpie, but no additional attributes from rlm_perl.ini when using httpie.
What am I missing here? It seems I missed some policy to have this working.
Thanks!!!