PrivacyIDEA, the application itself, can only communicate via a HTTP REST API. To augment this “limitation” there are a number of plugins that convert from one protocol or API into PrivacyIDEA’s REST API.
So when you use httpie, you are communicating directly with PrivacyIDEA, bypassing the PrivacyIDEA-RADIUS plugin. When you attempt to authenticate through the Fortigate, it is communicating via RADIUS, which is picked up by the PrivacyIDEA-RADIUS plugin, converted to a REST request, and passed along to PrivacyIDEA.
A better, equivilent test is to use radclient from your PrivacyIDEA server.
echo "User-Name=user, User-Password=password" | radclient -sx 127.0.0.1 \
auth secret_here
Note: For this to work, your freeradius clients.conf file will need to include an entry for itself, something like
client localhost {
ipaddr = 127.0.0.1
proto = *
netmask = 32
secret = secret_here
nastype = other
}
Running radclient with -sx will cause it to run in debug mode and print out a summary. This should help with troubleshooting.
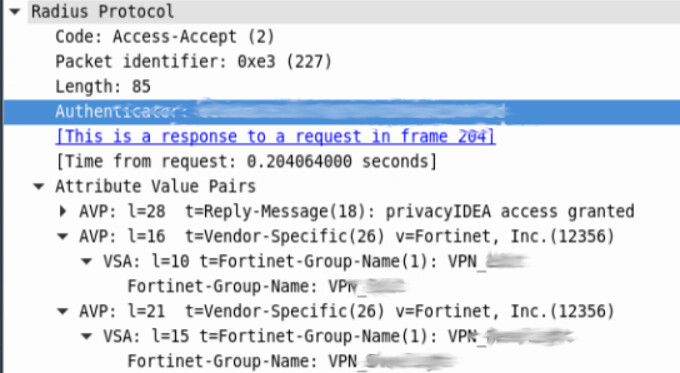
On the Fortigate side, the User Group you’ve created needs to match what PrivacyIDEA is passing back. If your rlm_perl.ini is configured to match CN=VPNgroupname,CN=Users,DC=somedomain,DC=com, then the user group in the Fortigate needs to be exactly that. If you are using a regex, which I would recommend, like regex = CN=(VPNgroupname).*, then you only need to enter VPNgroupname in the Fortigate User group. Regex would allow you to match on multiple groups and create multiple Fortigate user groups. Use the regex | which acts as an OR to the statement to match on multiple groups
regex = CN=(VPNGroup1|VPNGroup2|VPNGroup3).*
The above will pass VPNGroup1, VPNGroup2, or VPNGroup3 back to the Fortigate. An issue I ran into with the Fortigate, it will only take ONE value for Fortinet-Group-Name. So if a user is a member of VPNGroup1 and VPNGroup2, the Fortigate will only put the user in the last group it receives from the PrivacyIDEA-RADIUS plugin.
In addition to the user group, you also need a firewall policy to allow this authenticating traffic to flow through. The source needs to include the VPN subnet assigned to the portal as well as the user group.