At this moment we have. OVPN > NPS > FreeRadius > PrivacyIdea
PrivacyIdea authenticate user perfectly as you see, but something wrong in freeradius.
Could you check for the reasons of errors.
Ultimately I wannt to use push tokens
Wed Oct 5 20:26:46 2022 : Info: rlm_perl: Config File /etc/privacyidea/rlm_perl.ini found!
Wed Oct 5 20:26:46 2022 : Info: rlm_perl: Debugging config: true
Wed Oct 5 20:26:46 2022 : Info: rlm_perl: Default URL https://2fa.xxxxxxx/validate/check.
Wed Oct 5 20:26:46 2022 : Info: rlm_perl: Looking for config for auth-type Perl
Wed Oct 5 20:26:46 2022 : rlm_perl: RAD_REQUEST: NAS-Port-Type = Async
Wed Oct 5 20:26:46 2022 : rlm_perl: RAD_REQUEST: Calling-Station-Id = 83.xx.xx.xx
Wed Oct 5 20:26:46 2022 : rlm_perl: RAD_REQUEST: Called-Station-Id = 192.168.1.12
Wed Oct 5 20:26:46 2022 : rlm_perl: RAD_REQUEST: User-Password = pG9u1C0krDIglkUGzm4q906879
Wed Oct 5 20:26:46 2022 : rlm_perl: RAD_REQUEST: User-Name = username
Wed Oct 5 20:26:46 2022 : rlm_perl: RAD_REQUEST: NAS-Port = 15728719
Wed Oct 5 20:26:46 2022 : rlm_perl: RAD_REQUEST: NAS-Identifier = vpn
Wed Oct 5 20:26:46 2022 : rlm_perl: RAD_REQUEST: NAS-IP-Address = 192.168.0.1
Wed Oct 5 20:26:46 2022 : rlm_perl: RAD_REQUEST: Service-Type = Framed-User
Wed Oct 5 20:26:46 2022 : rlm_perl: RAD_REQUEST: Acct-Session-Id = 81500048
Wed Oct 5 20:26:46 2022 : rlm_perl: RAD_REQUEST: Packet-Src-IP-Address = 192.168.0.10
Wed Oct 5 20:26:46 2022 : rlm_perl: RAD_REQUEST: Framed-Protocol = PPP
Wed Oct 5 20:26:46 2022 : rlm_perl: RAD_REQUEST: Proxy-State = 0xfe80000000000000cc467de36e674294000000bd
Wed Oct 5 20:26:46 2022 : Info: rlm_perl: Password encoding guessed: ascii
Wed Oct 5 20:26:46 2022 : Info: rlm_perl: Setting client IP to 192.168.0.1.
Wed Oct 5 20:26:46 2022 : Info: rlm_perl: Auth-Type: Perl
Wed Oct 5 20:26:46 2022 : Info: rlm_perl: url: https://2fa.xxxxxxxxx/validate/check
Wed Oct 5 20:26:46 2022 : Info: rlm_perl: user sent to privacyidea: username
Wed Oct 5 20:26:46 2022 : Info: rlm_perl: realm sent to privacyidea: realm
Wed Oct 5 20:26:46 2022 : Info: rlm_perl: resolver sent to privacyidea: realm
Wed Oct 5 20:26:46 2022 : Info: rlm_perl: client sent to privacyidea: 192.168.0.1
Wed Oct 5 20:26:46 2022 : Info: rlm_perl: state sent to privacyidea:.
Wed Oct 5 20:26:46 2022 : rlm_perl: urlparam user = username.
Wed Oct 5 20:26:46 2022 : rlm_perl: urlparam resConf = test.
Wed Oct 5 20:26:46 2022 : rlm_perl: urlparam pass = pG9u1C0krDIglkUGzm4q906879.
Wed Oct 5 20:26:46 2022 : rlm_perl: urlparam client = 192.168.0.1.
Wed Oct 5 20:26:46 2022 : rlm_perl: urlparam realm = realm.
Wed Oct 5 20:26:46 2022 : Info: rlm_perl: Request timeout: 10.
Wed Oct 5 20:26:47 2022 : Info: rlm_perl: elapsed time for privacyidea call: 0.625667
Wed Oct 5 20:26:47 2022 : rlm_perl: Content {"detail": {"message": "matching 1 tokens", "otplen": 6, "serial": "OATH00000824", "threadid": 140707509860096, "type": "hotp", "user": {"surnam
Wed Oct 5 20:26:47 2022 : Info: rlm_perl: privacyIDEA access granted for username realm='realm'
Wed Oct 5 20:26:47 2022 : Info: rlm_perl: ++++ Parsing group: Mapping.
Wed Oct 5 20:26:47 2022 : Info: rlm_perl: +++++ Found member 'Mapping user'
Wed Oct 5 20:26:47 2022 : Info: rlm_perl: ++++++ Map: user : group -> Class
Wed Oct 5 20:26:47 2022 : Info: rlm_perl: ++++ Parsing group: Attribute.
Wed Oct 5 20:26:47 2022 : Info: rlm_perl: +++++ Found member 'Attribute Filter-Id'
Wed Oct 5 20:26:47 2022 : Info: rlm_perl: ++++++ Attribute: IF ''->'' == '' THEN 'Filter-Id'
Wed Oct 5 20:26:47 2022 : Info: rlm_perl: ++++++ no directory
Wed Oct 5 20:26:47 2022 : Info: rlm_perl: +++++++ User attribute is a string:.
Wed Oct 5 20:26:47 2022 : Info: rlm_perl: +++++++ trying to match.
Wed Oct 5 20:26:47 2022 : Info: rlm_perl: ++++++++ Result: No match, no RADIUS attribute Filter-Id added.
Wed Oct 5 20:26:47 2022 : Info: rlm_perl: +++++ Found member 'Attribute otherAttribute'
Wed Oct 5 20:26:47 2022 : Info: rlm_perl: ++++++ Attribute: IF ''->'' == '' THEN 'otherAttribute'
Wed Oct 5 20:26:47 2022 : Info: rlm_perl: ++++++ no directory
Wed Oct 5 20:26:47 2022 : Info: rlm_perl: +++++++ User attribute is a string:.
Wed Oct 5 20:26:47 2022 : Info: rlm_perl: +++++++ trying to match.
Wed Oct 5 20:26:47 2022 : Info: rlm_perl: ++++++++ Result: No match, no RADIUS attribute otherAttribute added.
Wed Oct 5 20:26:47 2022 : Info: rlm_perl: +++++ Found member 'Attribute Class'
Wed Oct 5 20:26:47 2022 : Info: rlm_perl: ++++++ Attribute: IF ''->'' == '' THEN 'Class'
Wed Oct 5 20:26:47 2022 : Info: rlm_perl: ++++++ no directory
Wed Oct 5 20:26:47 2022 : Info: rlm_perl: +++++++ User attribute is a string:.
Wed Oct 5 20:26:47 2022 : Info: rlm_perl: +++++++ trying to match.
Wed Oct 5 20:26:47 2022 : Info: rlm_perl: ++++++++ Result: No match, no RADIUS attribute Class added.
Wed Oct 5 20:26:47 2022 : Info: rlm_perl: return RLM_MODULE_OK
Wed Oct 5 20:26:55 2022 : Info: rlm_perl: Config File /etc/privacyidea/rlm_perl.ini found!
Wed Oct 5 20:26:55 2022 : Info: rlm_perl: Debugging config: true
Wed Oct 5 20:26:55 2022 : Info: rlm_perl: Default URL https://2fa.xxxxxxxx/validate/check.
Wed Oct 5 20:26:55 2022 : Info: rlm_perl: Looking for config for auth-type Perl
Wed Oct 5 20:26:55 2022 : rlm_perl: RAD_REQUEST: NAS-Port-Type = Async
Wed Oct 5 20:26:55 2022 : rlm_perl: RAD_REQUEST: Calling-Station-Id = 83.xx.xx.xx
Wed Oct 5 20:26:55 2022 : rlm_perl: RAD_REQUEST: Called-Station-Id = 192.168.1.12
Wed Oct 5 20:26:55 2022 : rlm_perl: RAD_REQUEST: User-Password = pG9u1C0krDIglkUGzm4q906879
Wed Oct 5 20:26:55 2022 : rlm_perl: RAD_REQUEST: User-Name = username
Wed Oct 5 20:26:55 2022 : rlm_perl: RAD_REQUEST: NAS-Port = 15728720
Wed Oct 5 20:26:55 2022 : rlm_perl: RAD_REQUEST: NAS-Identifier = vpn
Wed Oct 5 20:26:55 2022 : rlm_perl: RAD_REQUEST: NAS-IP-Address = 192.168.0.1
Wed Oct 5 20:26:55 2022 : rlm_perl: RAD_REQUEST: Service-Type = Framed-User
Wed Oct 5 20:26:55 2022 : rlm_perl: RAD_REQUEST: Acct-Session-Id = 81500049
Wed Oct 5 20:26:55 2022 : rlm_perl: RAD_REQUEST: Packet-Src-IP-Address = 192.168.0.10
Wed Oct 5 20:26:55 2022 : rlm_perl: RAD_REQUEST: Framed-Protocol = PPP
Wed Oct 5 20:26:55 2022 : rlm_perl: RAD_REQUEST: Proxy-State = 0xfe80000000000000cc467de36e674294000000be
Wed Oct 5 20:26:55 2022 : Info: rlm_perl: Password encoding guessed: ascii
Wed Oct 5 20:26:55 2022 : Info: rlm_perl: Setting client IP to 192.168.0.1.
Wed Oct 5 20:26:55 2022 : Info: rlm_perl: Auth-Type: Perl
Wed Oct 5 20:26:55 2022 : Info: rlm_perl: url: https://2fa.xxxxxxxxxx/validate/check
Wed Oct 5 20:26:55 2022 : Info: rlm_perl: user sent to privacyidea: username
Wed Oct 5 20:26:55 2022 : Info: rlm_perl: realm sent to privacyidea: realm
Wed Oct 5 20:26:55 2022 : Info: rlm_perl: resolver sent to privacyidea: realm
Wed Oct 5 20:26:55 2022 : Info: rlm_perl: client sent to privacyidea: 192.168.0.1
Wed Oct 5 20:26:55 2022 : Info: rlm_perl: state sent to privacyidea:.
Wed Oct 5 20:26:55 2022 : rlm_perl: urlparam user = username
Wed Oct 5 20:26:55 2022 : rlm_perl: urlparam resConf = test.
Wed Oct 5 20:26:55 2022 : rlm_perl: urlparam pass = pG9u1C0krDIglkUGzm4q906879.
Wed Oct 5 20:26:55 2022 : rlm_perl: urlparam client = 192.168.0.1.
Wed Oct 5 20:26:55 2022 : rlm_perl: urlparam realm = realm
Wed Oct 5 20:26:55 2022 : Info: rlm_perl: Request timeout: 10.
Wed Oct 5 20:26:55 2022 : Info: rlm_perl: elapsed time for privacyidea call: 0.261565
Wed Oct 5 20:26:55 2022 : rlm_perl: Content {"detail": {"message": "wrong otp value. previous otp used again", "otplen": 6, "serial": "OATH00000824", "threadid": 140707509860096, "type": "
Wed Oct 5 20:26:55 2022 : Info: rlm_perl: privacyIDEA Result status is true!
Wed Oct 5 20:26:55 2022 : Info: rlm_perl: privacyIDEA access denied for username realm='realm'
Wed Oct 5 20:26:55 2022 : Info: rlm_perl: return RLM_MODULE_REJECT
privacyIDEA configuration documentation
=======================================
* System: privacyidea
* Date: 2022-10-05 20:38
PI.cfg
------
PI_AUDIT_KEY_PRIVATE: **/etc/privacyidea/private.pem**
PI_AUDIT_KEY_PUBLIC: **/etc/privacyidea/public.pem**
PI_AUDIT_MODULE: **privacyidea.lib.auditmodules.sqlaudit**
PI_CUSTOM_CSS: **False**
PI_ENCFILE: **/etc/privacyidea/enckey**
PI_EXTERNAL_LINKS: **True**
PI_HSM: **default**
PI_LOGFILE: **/var/log/privacyidea/privacyidea.log**
PI_LOGLEVEL: **20**
PI_PEPPER: **redacted**
PI_VASCO_LIBRARY: **None**
For security reason we do not display the SQL URI, as it may contain the
database credentials.
SUPERUSER_REALM: **['super']**
.. note:: The SUPERUSER_REALM is a list of defined realms where the users
will have administrative rights when logging in to the web UI.
PI_AUDIT_POOL_SIZE: **20**
PI_AUDIT_SQL_TRUNCATE: **True**
PI_ENGINE_REGISTRY_CLASS: **shared**
Local Admins
------------
In addition to the SUPERUSER_REALM there are local administrators stored in
the database. The following administrators are defined:
* **admin** <admin@xxxxxxxxx>
System Base Configuration
-------------------------
__timestamp__: **1664990926**
email.tls: **0**
hotp.hashlib: **sha512**
radius.dictfile: **/etc/privacyidea/dictionary**
radius.identifier: **FreeRadius**
remote.verify_ssl_certificate: **0**
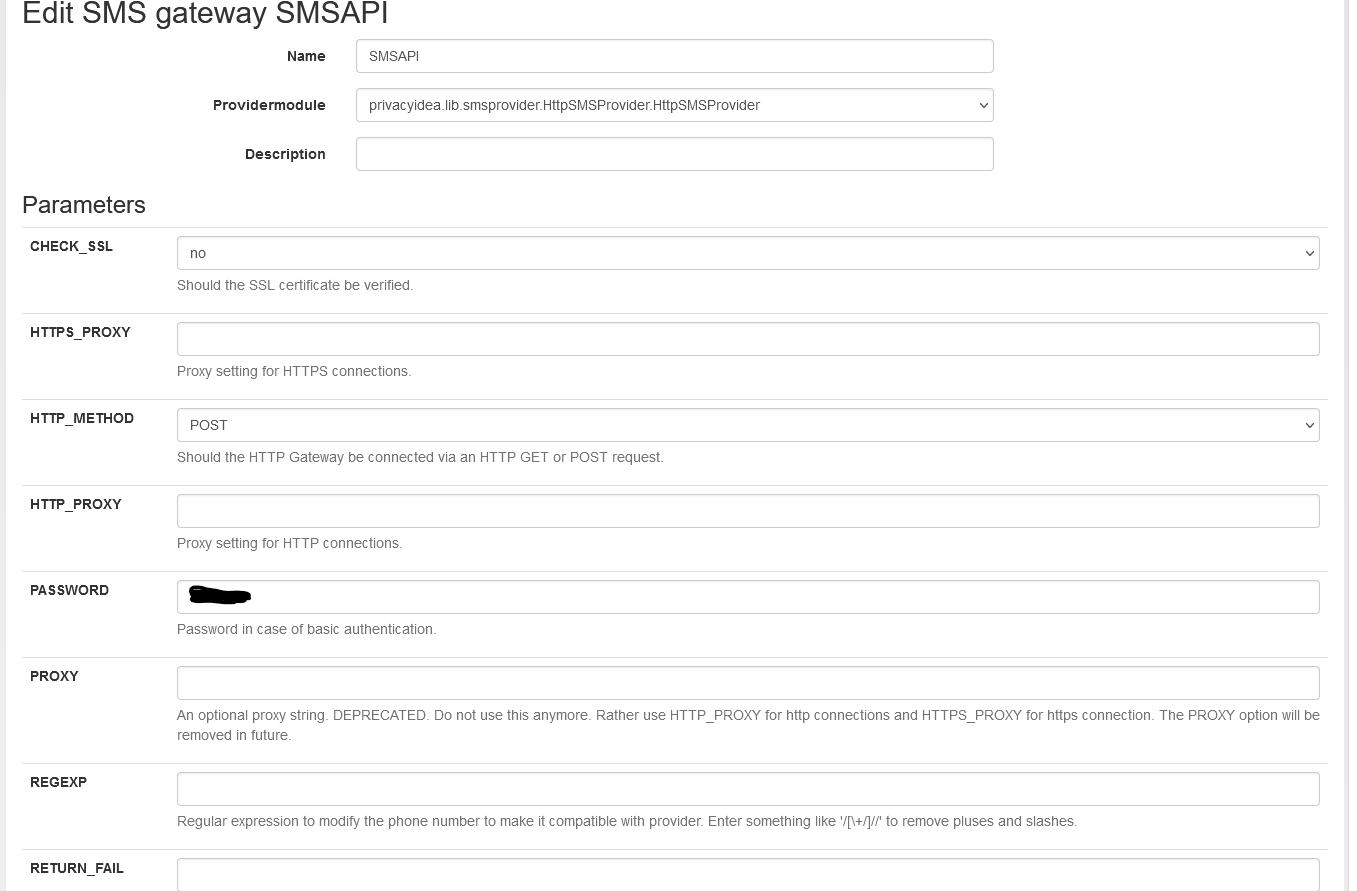
sms.Provider: **privacyidea.lib.smsprovider.HttpSMSProvider.HttpSMSProvider**
totp.hashlib: **sha1**
totp.timeStep: **30**
PrependPin: **True**
splitAtSign: **True**
IncFailCountOnFalsePin: **True**
ReturnSamlAttributes: **True**
Resolver Configuration
----------------------
The following resolvers are defined. Resolvers are connections to user stores.
To learn more about resolvers read [#resolvers]_.
deflocal
~~~~~~~~~~~~~~~~~~
* Name of the resolver: deflocal
* Type of the resolver: passwdresolver
Configuration
.............
filename: **/etc/passwd**
xxxxx
~~~~~~~~~~~~~~~~~~
* Name of the resolver: xxxxxxxx
* Type of the resolver: ldapresolver
Configuration
.............
SIZELIMIT: **500**
TIMEOUT: **60**
UIDTYPE: **objectGUID**
AUTHTYPE: **Simple**
SCOPE: **SUBTREE**
CACHE_TIMEOUT: **120**
NOSCHEMAS: **False**
TLS_VERIFY: **True**
TLS_VERSION: **2**
START_TLS: **False**
SERVERPOOL_ROUNDS: **5**
SERVERPOOL_SKIP: **60**
LDAPURI: **ldap://dc1.xxxxxxxxx**
LDAPBASE: **cn=users,dc=xxxxxx,dc=xxxxx,dc=xxxx**
LOGINNAMEATTRIBUTE: **sAMAccountName**
LDAPSEARCHFILTER: **(&(|(objectclass=person))(|(|(memberof=CN=terminal,CN=Users,DC=xxxxxx,DC=xxxxx,DC=xxxxxx)(primaryGroupID=1143))))**
USERINFO: **{ "phone" : "telephoneNumber", "mobile" : "mobile", "email" : "mail", "surname" : "sn", "givenname" : "givenName" }**
NOREFERRALS: **True**
EDITABLE: **False**
SERVERPOOL_PERSISTENT: **False**
BINDDN: **cn=ldap,cn=users,dc=xxxxxx,dc=xxxxxx,dc=xxxxxx**
BINDPW: **oiL6olKu8AmFADlWo4KT**
Realm Configuration
-------------------
Several resolvers are grouped into realms.
To learn more about realms read [#realms]_.
The following realms have been defined from the resolvers:
xxxxxxxxx
~~~~~~~~~~~~~~~
* Name of the realm: xxxxxxxxxx
**This is the default realm!**
Users in the default realm can authenticate without specifying the realm.
Users not in the default realm always need to specify the realm.
The following resolvers are configured in this realm:
* Name: xxxxxxxx
Priority: None
Type: ldapresolver
Policy Configuration
--------------------
Policies define the behaviour of privacyIDEA.
To learn more about policies read [#policies]_.
The following policies are defined in your system:
enroll_tokenlabel
~~~~~~~~~~~~~~~~~
active: **True**
scope: **enrollment**
realm: **['xxxxxxxx']**
adminrealm: **[]**
adminuser: **[]**
resolver: **['xxxxxxxxx']**
pinode: **['localnode']**
check_all_resolvers: **False**
user: **[]**
client: **[]**
time: ****
conditions: **[]**
priority: **1**
action: **{'push_firebase_configuration': 'poll only', 'push_registration_url': 'https://2fa.xxxxxxxxxx/ttype/push', 'push_ssl_verify': '1'}**
Authentication
~~~~~~~~~~~~~~~~~
active: **True**
scope: **authentication**
realm: **['xxxxxxxx']**
adminrealm: **[]**
adminuser: **[]**
resolver: **['xxxxxxx']**
pinode: **[]**
check_all_resolvers: **False**
user: **[]**
client: **[]**
time: ****
conditions: **[]**
priority: **1**
action: **{'challenge_response': 'push', 'challenge_text': 'test test', 'push_allow_polling': 'allow', 'push_ssl_verify': '0', 'push_text_on_mobile': 'question', 'push_title_on_mobile': 'Tittle', 'push_wait': '90', 'otppin': 'userstore'}**
Authorization
~~~~~~~~~~~~~~~~~
active: **True**
scope: **authorization**
realm: **['xxxxxxx']**
adminrealm: **[]**
adminuser: **[]**
resolver: **['xxxxxxx']**
pinode: **['localnode']**
check_all_resolvers: **False**
user: **[]**
client: **[]**
time: ****
conditions: **[]**
priority: **1**
action: **{'add_user_in_response': True, 'application_tokentype': True}**
Machine Configuration
---------------------
**TODO**
Token Configuration
-------------------
**TODO**
CA Configuration
----------------
**TODO**
.. [#resolvers] http://privacyidea.readthedocs.org/en/latest/configuration/useridresolvers.htm
.. [#realms] http://privacyidea.readthedocs.org/en/latest/configuration/realms.html
.. [#policies] http://privacyidea.readthedocs.org/en/latest/policies/index.html