hi
please help me config 2fa on Fortigate
- set up privateidea on ubuntu 18.04. according to instructions.
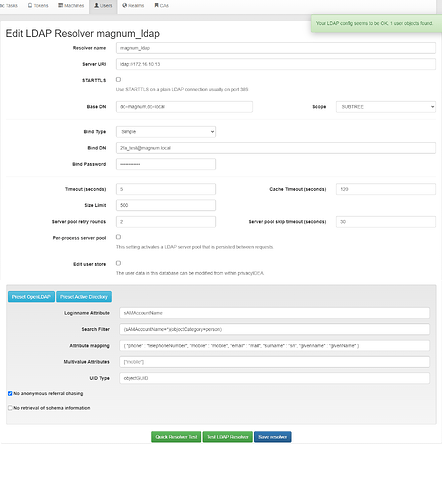
- created realm and ldapresolver, configured fortigate version 6.4.8
- on fortigate created a group and set up a connection to the radius server
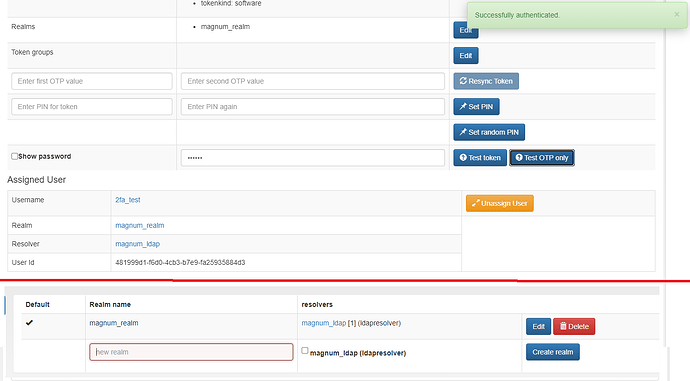
- created a token token and tied it to a test user
the problem is that on the forticlient it does not request a pin from the google authenticator and
connects to the ssl-vpn
tell me please what’s wrong, maybe something needs to be adjusted
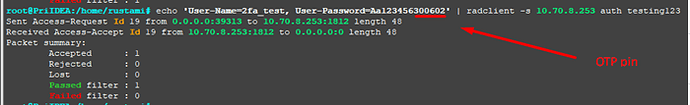
LOG from radius
(12) Received Access-Request Id 236 from 10.10.11.4:12305 to 10.70.8.253:1812 length 120
(12) NAS-Identifier = “magnum”
(12) User-Name = “2fa_test”
(12) User-Password = “Aa123456”
(12) Framed-IP-Address = 176.64.30.212
(12) NAS-Port = 8
(12) NAS-Port-Type = Virtual
(12) Calling-Station-Id = “176.64.30.212”
(12) Acct-Session-Id = “60fee9a7”
(12) Connect-Info = “vpn-ssl”
(12) Fortinet-Vdom-Name = “root”
(12) # Executing section authorize from file /etc/freeradius/3.0/sites-enabled/privacyidea
(12) authorize {
(12) update request {
(12) EXPAND %{Packet-Src-IP-Address}
(12) → 10.10.11.4
(12) Packet-Src-IP-Address = 10.10.11.4
(12) } # update request = noop
(12) perl-privacyidea: $RAD_REQUEST{‘User-Name’} = &request:User-Name → ‘2fa_test’
(12) perl-privacyidea: $RAD_REQUEST{‘User-Password’} = &request:User-Password → ‘Aa123456’
(12) perl-privacyidea: $RAD_REQUEST{‘NAS-Port’} = &request:NAS-Port → ‘8’
(12) perl-privacyidea: $RAD_REQUEST{‘Framed-IP-Address’} = &request:Framed-IP-Address → ‘176.64.30.212’
(12) perl-privacyidea: $RAD_REQUEST{‘Calling-Station-Id’} = &request:Calling-Station-Id → ‘176.64.30.212’
(12) perl-privacyidea: $RAD_REQUEST{‘NAS-Identifier’} = &request:NAS-Identifier → ‘magnum’
(12) perl-privacyidea: $RAD_REQUEST{‘NAS-Port-Type’} = &request:NAS-Port-Type → ‘Virtual’
(12) perl-privacyidea: $RAD_REQUEST{‘Acct-Session-Id’} = &request:Acct-Session-Id → ‘60fee9a7’
(12) perl-privacyidea: $RAD_REQUEST{‘Connect-Info’} = &request:Connect-Info → ‘vpn-ssl’
(12) perl-privacyidea: $RAD_REQUEST{‘Fortinet-Vdom-Name’} = &request:Fortinet-Vdom-Name → ‘root’
(12) perl-privacyidea: $RAD_REQUEST{‘Packet-Src-IP-Address’} = &request:Packet-Src-IP-Address → ‘10.10.11.4’
(12) perl-privacyidea: &request:Fortinet-Vdom-Name = $RAD_REQUEST{‘Fortinet-Vdom-Name’} → ‘root’
(12) perl-privacyidea: &request:Connect-Info = $RAD_REQUEST{‘Connect-Info’} → ‘vpn-ssl’
(12) perl-privacyidea: &request:Acct-Session-Id = $RAD_REQUEST{‘Acct-Session-Id’} → ‘60fee9a7’
(12) perl-privacyidea: &request:User-Password = $RAD_REQUEST{‘User-Password’} → ‘Aa123456’
(12) perl-privacyidea: &request:Calling-Station-Id = $RAD_REQUEST{‘Calling-Station-Id’} → ‘176.64.30.212’
(12) perl-privacyidea: &request:NAS-Port = $RAD_REQUEST{‘NAS-Port’} → ‘8’
(12) perl-privacyidea: &request:NAS-Port-Type = $RAD_REQUEST{‘NAS-Port-Type’} → ‘Virtual’
(12) perl-privacyidea: &request:Packet-Src-IP-Address = $RAD_REQUEST{‘Packet-Src-IP-Address’} → ‘10.10.11.4’
(12) perl-privacyidea: &request:User-Name = $RAD_REQUEST{‘User-Name’} → ‘2fa_test’
(12) perl-privacyidea: &request:Framed-IP-Address = $RAD_REQUEST{‘Framed-IP-Address’} → ‘176.64.30.212’
(12) perl-privacyidea: &request:NAS-Identifier = $RAD_REQUEST{‘NAS-Identifier’} → ‘magnum’
(12) [perl-privacyidea] = ok
(12) if (ok || updated) {
(12) if (ok || updated) → TRUE
(12) if (ok || updated) {
(12) update control {
(12) Auth-Type := Perl
(12) } # update control = noop
(12) } # if (ok || updated) = noop
(12) } # authorize = ok
(12) Found Auth-Type = Perl
(12) # Executing group from file /etc/freeradius/3.0/sites-enabled/privacyidea
(12) Auth-Type Perl {
(12) perl-privacyidea: $RAD_REQUEST{‘User-Name’} = &request:User-Name → ‘2fa_test’
(12) perl-privacyidea: $RAD_REQUEST{‘User-Password’} = &request:User-Password → ‘Aa123456’
(12) perl-privacyidea: $RAD_REQUEST{‘NAS-Port’} = &request:NAS-Port → ‘8’
(12) perl-privacyidea: $RAD_REQUEST{‘Framed-IP-Address’} = &request:Framed-IP-Address → ‘176.64.30.212’
(12) perl-privacyidea: $RAD_REQUEST{‘Calling-Station-Id’} = &request:Calling-Station-Id → ‘176.64.30.212’
(12) perl-privacyidea: $RAD_REQUEST{‘NAS-Identifier’} = &request:NAS-Identifier → ‘magnum’
(12) perl-privacyidea: $RAD_REQUEST{‘NAS-Port-Type’} = &request:NAS-Port-Type → ‘Virtual’
(12) perl-privacyidea: $RAD_REQUEST{‘Acct-Session-Id’} = &request:Acct-Session-Id → ‘60fee9a7’
(12) perl-privacyidea: $RAD_REQUEST{‘Connect-Info’} = &request:Connect-Info → ‘vpn-ssl’
(12) perl-privacyidea: $RAD_REQUEST{‘Fortinet-Vdom-Name’} = &request:Fortinet-Vdom-Name → ‘root’
(12) perl-privacyidea: $RAD_REQUEST{‘Packet-Src-IP-Address’} = &request:Packet-Src-IP-Address → ‘10.10.11.4’
(12) perl-privacyidea: $RAD_CHECK{‘Auth-Type’} = &control:Auth-Type → ‘Perl’
(12) perl-privacyidea: $RAD_CONFIG{‘Auth-Type’} = &control:Auth-Type → ‘Perl’
rlm_perl: Config File /etc/privacyidea/rlm_perl.ini found!
rlm_perl: Debugging config: true
rlm_perl: Default URL https://10.70.8.253/validate/check
rlm_perl: Looking for config for auth-type Perl
rlm_perl: RAD_REQUEST: Fortinet-Vdom-Name = root
rlm_perl: RAD_REQUEST: Connect-Info = vpn-ssl
rlm_perl: RAD_REQUEST: Acct-Session-Id = 60fee9a7
rlm_perl: RAD_REQUEST: User-Password = Aa123456
rlm_perl: RAD_REQUEST: Calling-Station-Id = 176.64.30.212
rlm_perl: RAD_REQUEST: NAS-Port = 8
rlm_perl: RAD_REQUEST: NAS-Port-Type = Virtual
rlm_perl: RAD_REQUEST: Packet-Src-IP-Address = 10.10.11.4
rlm_perl: RAD_REQUEST: User-Name = 2fa_test
rlm_perl: RAD_REQUEST: Framed-IP-Address = 176.64.30.212
rlm_perl: RAD_REQUEST: NAS-Identifier = magnum
rlm_perl: Password encoding guessed: ascii
rlm_perl: Setting client IP to 10.10.11.4.
rlm_perl: Auth-Type: Perl
rlm_perl: url: https://10.70.8.253/validate/check
rlm_perl: user sent to privacyidea: 2fa_test
rlm_perl: realm sent to privacyidea: magnum_realm
rlm_perl: resolver sent to privacyidea: magnum_ldap
rlm_perl: client sent to privacyidea: 10.10.11.4
rlm_perl: state sent to privacyidea:
rlm_perl: urlparam resConf = magnum_ldap
rlm_perl: urlparam user = 2fa_test
rlm_perl: urlparam pass = Aa123456
rlm_perl: urlparam client = 10.10.11.4
rlm_perl: urlparam realm = magnum_realm
rlm_perl: Request timeout: 20
rlm_perl: Not verifying SSL certificate!
rlm_perl: elapsed time for privacyidea call: 2.151159
rlm_perl: Content {“detail”: {“client_mode”: “interactive”, “message”: “:, :, :”, “messages”: [“:”, “:”, “:”], “multi_challenge”: [{“client_mode”: “interactive”, “message”: “:”, “serial”: “OATH000087F8”, “transaction_id”: “13018195230672367535”, “type”: “hotp”}, {“client_mode”: “interactive”, “message”: “:”, “serial”: “TOTP00008694”, “transaction_id”: “13018195230672367535”, “type”: “totp”}, {“client_mode”: “interactive”, “message”: “:”, “serial”: “TOTP0001D5DA”, “transaction_id”: “13018195230672367535”, “type”: “totp”}], “serial”: “TOTP0001D5DA”, “threadid”: 140432084944640, “transaction_id”: “13018195230672367535”, “transaction_ids”: [“13018195230672367535”, “13018195230672367535”, “13018195230672367535”], “type”: “totp”, “preferred_client_mode”: “interactive”}, “id”: 2, “jsonrpc”: “2.0”, “result”: {“authentication”: “CHALLENGE”, “status”: true, “value”: false}, “time”: 1681812160.8520744, “version”: “privacyIDEA 3.8.1”, “versionnumber”: “3.8.1”, “signature”: “rsa_sha256_pss:577de0546a8efabb9e4cfb9f944df20f334227e3b9a4abcb06c1b168931d8f73576730bbdfca451563a5f3325df830cd7525c83058c8f746c44ab49714d99b42f6291aa38ecfc095d95567d6db17fb91280c330fe935dbc96c04fbe486e175343159000d658bf155f9e17190b62b21e5c4e64a820814914b31e6224d01705345511ae0948c3aec74150b2faac8de066d5a1e71b2bc857126073e85e6b6f436e9717af323e6b7ad0027c5dca3a419ac810bc845f15f6ffea1feddb4332301e3b69a33b0995612b0ae111484d9ac066fea011607d8ad8b8c04b60cbe360e62c878f3efac143367a36024dcc9d0044d413f6bb35acf4959a6bb4e422785c5c9b8dc”}
rlm_perl: privacyIDEA Result status is true!
rlm_perl: ++++ Parsing group: Attribute
rlm_perl: +++++ Found member ‘Attribute Filter-Id’
rlm_perl: ++++++ Attribute: IF ‘’->‘’ == ‘’ THEN ‘Filter-Id’
rlm_perl: ++++++ no directory
rlm_perl: +++++++ User attribute is a string:
rlm_perl: +++++++ trying to match
rlm_perl: ++++++++ Result: No match, no RADIUS attribute Filter-Id added.
rlm_perl: +++++ Found member ‘Attribute otherAttribute’
rlm_perl: ++++++ Attribute: IF ‘’->‘’ == ‘’ THEN ‘otherAttribute’
rlm_perl: ++++++ no directory
rlm_perl: +++++++ User attribute is a string:
rlm_perl: +++++++ trying to match
rlm_perl: ++++++++ Result: No match, no RADIUS attribute otherAttribute added.
rlm_perl: +++++ Found member ‘Attribute Class’
rlm_perl: ++++++ Attribute: IF ‘’->‘’ == ‘’ THEN ‘Class’
rlm_perl: ++++++ no directory
rlm_perl: +++++++ User attribute is a string:
rlm_perl: +++++++ trying to match
rlm_perl: ++++++++ Result: No match, no RADIUS attribute Class added.
rlm_perl: ++++ Parsing group: Mapping
rlm_perl: +++++ Found member ‘Mapping user’
rlm_perl: ++++++ Map: user : group → Class
rlm_perl: return RLM_MODULE_HANDLED
(12) perl-privacyidea: &request:Fortinet-Vdom-Name = $RAD_REQUEST{‘Fortinet-Vdom-Name’} → ‘root’
(12) perl-privacyidea: &request:Connect-Info = $RAD_REQUEST{‘Connect-Info’} → ‘vpn-ssl’
(12) perl-privacyidea: &request:Acct-Session-Id = $RAD_REQUEST{‘Acct-Session-Id’} → ‘60fee9a7’
(12) perl-privacyidea: &request:User-Password = $RAD_REQUEST{‘User-Password’} → ‘Aa123456’
(12) perl-privacyidea: &request:Calling-Station-Id = $RAD_REQUEST{‘Calling-Station-Id’} → ‘176.64.30.212’
(12) perl-privacyidea: &request:NAS-Port = $RAD_REQUEST{‘NAS-Port’} → ‘8’
(12) perl-privacyidea: &request:NAS-Port-Type = $RAD_REQUEST{‘NAS-Port-Type’} → ‘Virtual’
(12) perl-privacyidea: &request:Packet-Src-IP-Address = $RAD_REQUEST{‘Packet-Src-IP-Address’} → ‘10.10.11.4’
(12) perl-privacyidea: &request:User-Name = $RAD_REQUEST{‘User-Name’} → ‘2fa_test’
(12) perl-privacyidea: &request:Framed-IP-Address = $RAD_REQUEST{‘Framed-IP-Address’} → ‘176.64.30.212’
(12) perl-privacyidea: &request:NAS-Identifier = $RAD_REQUEST{‘NAS-Identifier’} → ‘magnum’
(12) perl-privacyidea: &reply:State = $RAD_REPLY{‘State’} → ‘13018195230672367535’
(12) perl-privacyidea: &reply:Reply-Message = $RAD_REPLY{‘Reply-Message’} → ‘:, :, :’
(12) perl-privacyidea: ERROR: Internal failure creating pair &reply:Class += $RAD_REPLY{‘Class’} → ‘undef’
(12) perl-privacyidea: &control:Response-Packet-Type = $RAD_CHECK{‘Response-Packet-Type’} → ‘Access-Challenge’
(12) perl-privacyidea: &control:Auth-Type = $RAD_CHECK{‘Auth-Type’} → ‘Perl’
(12) [perl-privacyidea] = handled
(12) } # Auth-Type Perl = handled
(12) Using Post-Auth-Type Challenge
(12) Post-Auth-Type sub-section not found. Ignoring.
(12) Sent Access-Challenge Id 236 from 10.70.8.253:1812 to 10.10.11.4:12305 length 0
(12) State = 0x3133303138313935323330363732333637353335
(12) Reply-Message = “:, :, :”
(12) Finished request
Waking up in 4.9 seconds.
(12) Cleaning up request packet ID 236 with timestamp +587
Ready to process requests