Instead of continuing to hijack another thread, I’m starting a new one here. I recently integrated an SMS provider and am testing SMS tokens with PI 3.4. Basic functionality is currently working:
- User enters username and token PIN
- Authentication fails, triggering an SMS token
- User reauthenticates using PIN+SMS token
- Authentication success
What doesn’t appear to be working for me is FreeRADIUS sending back an Access-Challenge packet.
Currently, when a user authentications, they have to enter their PIN+OTP for the password field. I guess before going any further, is it possible to support both this current behavior and challenge response where a user enters their userstore password and then challenged for an SMS/Email token from the same authenticating application? For example:
Scenario A
User enters username and PIN+OTP (TOTP/HOTP)
User is authenticated
Scenario B
User enters username and user store password
SMS/Email token generated
RADIUS/application request challenge response
User enters SMS/Email token to challenge response
User is authenticated
As indicated in another thread, PrivacyIDEA/FreeRADIUS is capable of sending an Access-Challenge packet back to the authenticating application prompting the user for the challenge token. Another user has indicated successfully configuring PrivacyIDEA and associated applications of supporting this behavior. However, only the perl-based plugin works for challenge-response and attribute mapping.
I initially suspected that because I am using FreeRADIUS 3.0, I was using the rest-based plugin. However, I am successfully using attribute mapping for user VPN connections. Furthermore, digging into my configurations, it appears I really AM using the perl-based plugin, though with slight syntactical modifications to get it to work with FreeRADIUS 3.0.
/freeradius/3.0/mods-enabled/perl
perl {
filename = /usr/share/privacyidea/freeradius/privacyidea_radius.pm
}
/freeradius/3.0/sites-enabled/privacyidea
There’s a greater deviation on the site configuration under authentication. When adding the digest and unix modules, FreeRADIUS does not start. Though at the moment, I haven’t been able to troubleshoot why.
server {
authorize {
#files
perl-privacyidea
if (ok || updated) {
update control {
Auth-Type := Perl
}
}
}
listen {
type = auth
ipaddr = *
port = 0
}
authenticate {
Auth-Type Perl {
perl-privacyidea
}
}
}
/freeradius/3.0/users
DEFAULT Auth-type := perl
I’ve then got a configuration file under /etc/privacyidea/rlm_perl.ini where I specify basic configuration settings and attribute mapppings.
So it seems I’m using the proper plugin and have SMS token configuration setup properly, but the additional challenege response box for our vpn connection doesn’t appear as anticipated.
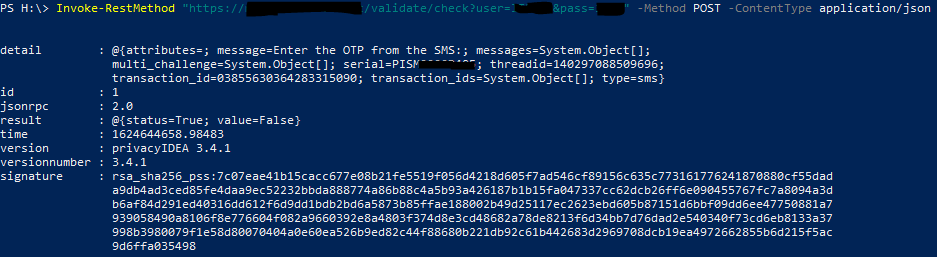
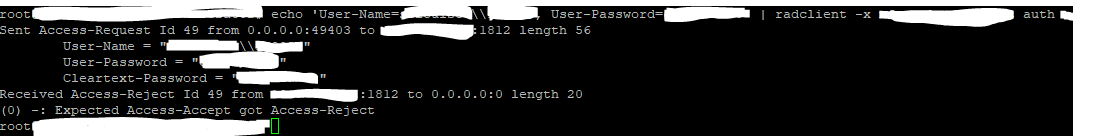
I’m assuming radclient would allow me to see the Access-Challenge response, but instead, all I get is an Access-Reject
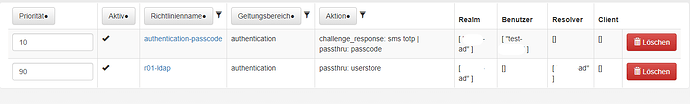
I have two policies setup
![]()
![]()
With the authentication policy enabled, my first authentication with user store credentials works and an SMS token is sent, but I still only get an Access-Reject. Attempting to authenticate using PIN+SMS OTP fails and generates another OTP.
So…I know I’m doing something wrong, but I’m not sure where. Any ideas?