First of all: everything works fine, there’s only one odd behaviour.
When logging into ownCloud the privacyIDEA Authenticator asks for confirmation. So far so good. What I would expect then is that I get automatically logged in after hitting the confirmation button. Instead I have to type in something into the OTP field (anything will do just to omit the ‘You have to type …’ message) and hit enter.
Is this by design or do I miss some setting?
I think the simple reason is, that the owncloud plugin available in the market place does not have the latest code. A lot, a lot of stuff was packed in 2019.
If you need to, just use the code from github.
Thanks for the reply.
I tried that. It makes things worse. Now the plugin wants a valid PIN, which does not exist because during enrollment none was created.
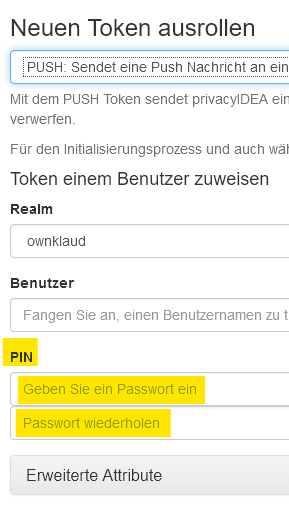
Which version of the privacyIDEA ownCLoud plugin do you have installed (e.g. version or github hash) on which version of ownCloud?
How do you have configured the ownCloud plugin? (You need the triggerchallenge)
I have installed privacyIDEA version 2.5.2. on owbCloud version 10.3.1
I tried this from GitHub: https://github.com/privacyidea/privacyidea-owncloud-app/tree/master. It still says 2.5.2 in appinfo.xml, but because the latest commit is dated Nov, 26 I thought that would be what you ment.
And in answer to your last question:
The - I assume (see last post) - latest version of the plugin gives me this (1st step after login):
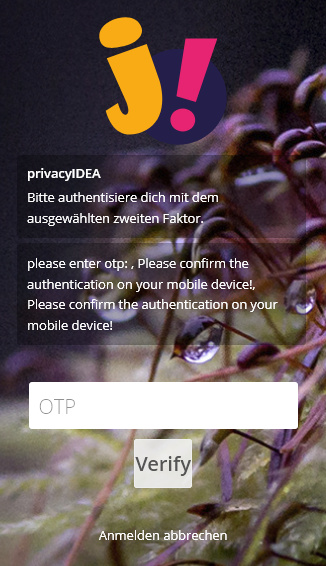
That’s fine, but I got some rather cosmetic remarks
- Translation missing
- Redundant multiple hints (which is probably due to the fact, that I’ve registered two tokens, but unnecessary and confusing)
- Rather messy formatting (please … otp:,Please …). Well, never mind.
Then I entered 0 (although there is no PIN defined for the token, just because the OTP field requires some input in order to make the Verify button work - which, btw, lacks translation as well). The current version of the plugin then grants access. The latest? version does this:
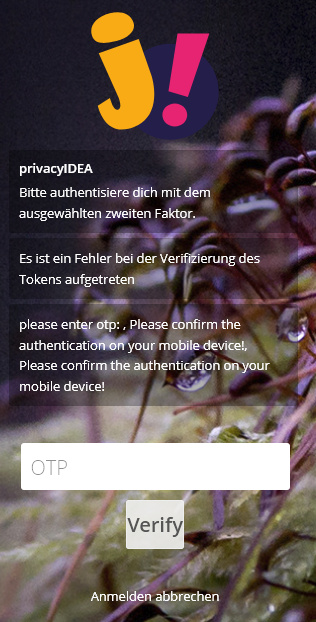
I guess it does not like my 0-PIN and would like to have some valid PIN - which does not exist. This latest? version also does not allow me to use the TOTP token. No matter if I use it rightaway or instead of 0.
In a nutshell: There’s no way of logging in anymore.
P.S.
That Verify button, please:
#body-login #piLoginForm input.button[type=“submit”] {
padding: 10px 15px;
}
Dear @joerg.giencke
the information you provided indicates that you did everything (at least what you mentioned) right.
Unfortunately you do not provide a lot of other information. Your previous comment
did not help a lot. Because the plugin never asks for “a valid PIN”.
So my personal problem is, that the hours I spent with guessing sum up a lot.
In your case I guess, that your expectations do not fix the implementation. Please note, that the plugin currently does not support in a nicely manner, that a user has a push token and another tokentype (like totp) at the same time.
You problem is, that the system is a complex software with a complex scenario.
If you want to go further down the road, you need to look at (not a complete list
- what do you expect the software to do
- what the software says it would do
- what the software actually does
- what the owncloud plugin says exactly
- which tokens a user has
- how privacyidea is configured
- what the audit log of privacyidea says
- what the log file of privacyidea says
Yes, and you are allowed to complain about the lack of documentation. Then I am allowed to complain about who actually is writing the documentation - and keeping it up to date.
Look at it - there is actually nearly 400 pages of documentation. Yes, it does not describe everything. It can not and will never.
Time is up. Need to do breakfast.
Oh I said to myself: “ignore him”. But is is so difficult. Read the docs!
Okay, ‘not nicely’, but it does. And I think you’re so  close.
close.
But, before we continue, let me make this quite clear: Schoolmasterly teachings about what my problems are are not very helpful in this context. I am seeing a software that actually does what I expect it to do - just not nicely. I am not complaining, I’m just trying to help, to improve things, to debug.
BTW, you’re of course right, the plugin is not asking for a ‘valid PIN’. I was confused because when an administrator enrolls a PUSH-token for somebody else he can, optionally and for what ever reason, define a PIN. Therefore I was under the impression the plugin was asking for a PIN. Sorry for that confusion.
Okay, I’ve tested the latest version again. This time just with one single PUSH-token existing. The good news is that it’s no longer asking for an OTP. The bad news is, that it doesn’t let me in. It just sits there and waits. And here I repeat myself: It makes things worse.
While the current plugin happily handles both, TOTP and PUSH, even simultaneously, just not nicely, the latest version does not let you in. I think the term ‘worse’ is justified in this case.
So, both versions do not automatically react on the signal that - my wild guess - firebase is sending. And whilst the current version at least leaves the option to trigger the log in with a ‘fake PIN’ the latest version locks you out.
If the current version would do what the latest version is supposed to do (but not does) - i.e. log one in automatically - everything would be perfect. You either hit the button in the authenticator or enter an OTP.
Feierabend.
I do not thing we continue. If anyone wants to stop guessing, please check my previous post: