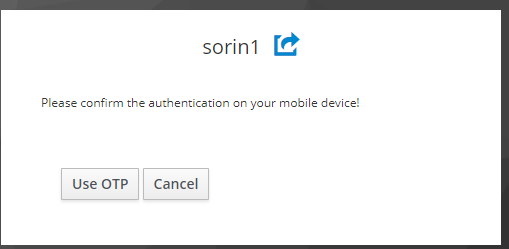
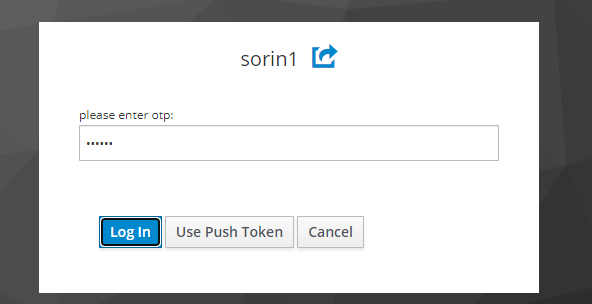
What am I missing? I checked all the policies. All of them, one by one. It’s not working. Also I checked SMS gateway for Push Token and System Config. I’m not getting the error and the server freeze when I enter on OTP form only password from userstore.
Thanks in advance.
Here’s my config:
privacyIDEA configuration documentation
- System: ubuntu
- Date: 2021-03-14 14:59
PI.cfg
PI_AUDIT_KEY_PRIVATE: /etc/privacyidea/private.pem
PI_AUDIT_KEY_PUBLIC: /etc/privacyidea/public.pem
PI_AUDIT_MODULE: privacyidea.lib.auditmodules.sqlaudit
PI_CUSTOM_CSS: False
PI_ENCFILE: /etc/privacyidea/enckey
PI_EXTERNAL_LINKS: True
PI_HSM: default
PI_LOGFILE: /var/log/privacyidea/privacyidea.log
PI_LOGLEVEL: 20
PI_PEPPER: redacted
PI_VASCO_LIBRARY: None
For security reason we do not display the SQL URI, as it may contain the
database credentials.
SUPERUSER_REALM: [‘super’]
… note:: The SUPERUSER_REALM is a list of defined realms where the users
will have administrative rights when logging in to the web UI.
PI_AUDIT_POOL_SIZE: 20
PI_AUDIT_SQL_TRUNCATE: True
PI_ENGINE_REGISTRY_CLASS: shared
Local Admins
In addition to the SUPERUSER_REALM there are local administrators stored in
the database. The following administrators are defined:
System Base Configuration
AutoResync: 1
DefaultMaxFailCount: 100
DefaultOtpLen: ****
email.tls: False
failcounter_clear_timeout: 5
hotp.hashlib: sha1
IncFailCountOnFalsePin: 1
no_auth_counter: 0
OverrideAuthorizationClient: ****
PrependPin: 1
radius.dictfile: /etc/privacyidea/dictionary
remote.verify_ssl_certificate: False
ReturnSamlAttributes: 1
ReturnSamlAttributesOnFail: 1
sms.Provider: privacyidea.lib.smsprovider.HttpSMSProvider.HttpSMSProvider
splitAtSign: 0
totp.hashlib: sha1
totp.timeStep: 30
UiLoginDisplayHelpButton: 0
UiLoginDisplayRealmBox: 0
timestamp: 1615758547
Resolver Configuration
The following resolvers are defined. Resolvers are connections to user stores.
To learn more about resolvers read [#resolvers]_.
deflocal
* Name of the resolver: deflocal
* Type of the resolver: passwdresolver
Configuration
.............
filename: **/etc/passwd**
myusers
- Name of the resolver: myusers
- Type of the resolver: passwdresolver
Configuration
…
fileName: /etc/passwd
resolver1
* Name of the resolver: resolver1
* Type of the resolver: sqlresolver
Configuration
.............
Database: **database**
Driver: **mysql**
Editable: **True**
Limit: **500**
Map: **{"userid": "uid", "username": "name", "email": "mail", "password": "pass" }**
Password: **sorin**
Password_Hash_Type: **SSHA256**
Server: **127.0.0.1**
Table: **user**
User: **admin**
test
- Name of the resolver: test
- Type of the resolver: sqlresolver
Configuration
…
Database: pi?charset=utf8
Driver: mysql+pymysql
Editable: 1
Limit: 500
Map: {“userid”: “id”, “username”: “username”, “email”:“email”, “password”: “password”, “phone”:“phone”, “mobile”:“mobile”, “surname”:“surname”, “givenname”:“givenname”, “description”: “description”}
Password: 30xINl_9BZbD
Server: localhost
Table: users_test
User: pi
ldap_resolver
* Name of the resolver: ldap_resolver
* Type of the resolver: ldapresolver
Configuration
.............
AUTHTYPE: **Simple**
BINDDN: ****
CACHE_TIMEOUT: **500**
DN_TEMPLATE: ****
EDITABLE: **False**
LDAPBASE: **ou=users,dc=example,dc=com**
LDAPSEARCHFILTER: **(uid=*)(objectClass=inetOrgPerson)**
LDAPURI: **ldap://localhost:10389**
LOGINNAMEATTRIBUTE: **uid**
NOREFERRALS: **True**
NOSCHEMAS: **False**
SCOPE: **SUBTREE**
SERVERPOOL_PERSISTENT: **False**
SERVERPOOL_ROUNDS: **5**
SERVERPOOL_SKIP: **500**
SIZELIMIT: **500**
START_TLS: **False**
TIMEOUT: **500**
TLS_VERIFY: **True**
UIDTYPE: **uid**
USERINFO: **{ "phone" : "telephoneNumber", "mobile" : "mobile", "email" : "mail", "surname" : "sn", "givenname" : "givenName"}**
Realm Configuration
-------------------
Several resolvers are grouped into realms.
To learn more about realms read [#realms]_.
The following realms have been defined from the resolvers:
defrealm
~~~~~~~~~~~~~~~
* Name of the realm: defrealm
The following resolvers are configured in this realm:
* Name: deflocal
Priority: None
Type: passwdresolver
internal_realm
~~~~~~~~~~~~~~~
* Name of the realm: internal_realm
**This is the default realm!**
Users in the default realm can authenticate without specifying the realm.
Users not in the default realm always need to specify the realm.
The following resolvers are configured in this realm:
* Name: ldap_resolver
Priority: None
Type: ldapresolver
Policy Configuration
--------------------
Policies define the behaviour of privacyIDEA.
To learn more about policies read [#policies]_.
The following policies are defined in your system:
pushauth
~~~~~~~~~~~~~~~~~
active: **True**
scope: **authentication**
realm: **['internal_realm']**
adminrealm: **[]**
adminuser: **[]**
resolver: **['ldap_resolver']**
pinode: **['localnode']**
check_all_resolvers: **False**
user: **[]**
client: **[]**
time: ****
conditions: **[]**
priority: **1**
action: **{'challenge_response': 'push hotp totp', 'otppin': 'userstore', 'passthru': 'userstore', 'push_allow_polling': 'allow', 'push_ssl_verify': '0', 'push_text_on_mobile': 'Please get bachelor degree!', 'push_title_on_mobile': 'Confirm this to login', 'push_wait': '9000', 'reset_all_user_tokens': True}**
authorization
~~~~~~~~~~~~~~~~~
active: **True**
scope: **authorization**
realm: **[]**
adminrealm: **[]**
adminuser: **[]**
resolver: **[]**
pinode: **[]**
check_all_resolvers: **False**
user: **[]**
client: **[]**
time: ****
conditions: **[]**
priority: **2**
action: **{'application_tokentype': True, 'tokentype': 'push hotp totp'}**
pushenroll
~~~~~~~~~~~~~~~~~
active: **True**
scope: **enrollment**
realm: **['internal_realm']**
adminrealm: **[]**
adminuser: **[]**
resolver: **['ldap_resolver']**
pinode: **[]**
check_all_resolvers: **False**
user: **[]**
client: **[]**
time: ****
conditions: **[]**
priority: **3**
action: **{'hotp_max_active_token_per_user': '1', 'hotp_max_token_per_user': '0', 'push_firebase_configuration': 'MyFirebaseProject', 'push_ssl_verify': '0', 'totp_max_active_token_per_user': '1', 'totp_max_token_per_user': '1'}**
user_policy
~~~~~~~~~~~~~~~~~
active: **True**
scope: **user**
realm: **['internal_realm']**
adminrealm: **[]**
adminuser: **[]**
resolver: **['ldap_resolver']**
pinode: **[]**
check_all_resolvers: **False**
user: **[]**
client: **[]**
time: ****
conditions: **[]**
priority: **4**
action: **{'delete': True, 'enrollHOTP': True, 'enrollPUSH': True, 'enrollTOTP': True, 'hotp_2step': 'allow', 'hotp_otplen': '6', 'totp_2step': 'allow', 'totp_otplen': '6'}**
webui1
~~~~~~~~~~~~~~~~~
active: **True**
scope: **webui**
realm: **[]**
adminrealm: **[]**
adminuser: **[]**
resolver: **[]**
pinode: **[]**
check_all_resolvers: **False**
user: **[]**
client: **[]**
time: ****
conditions: **[]**
priority: **5**
action: **{'default_tokentype': 'push', 'hide_buttons': True, 'hide_welcome_info': True, 'login_mode': 'privacyIDEA', 'login_text': 'Please get bachelor degree', 'logout_time': '1200'}**
Machine Configuration
---------------------
**TODO**
Token Configuration
-------------------
**TODO**
CA Configuration
----------------
**TODO**
.. [#resolvers] http://privacyidea.readthedocs.org/en/latest/configuration/useridresolvers.htm
.. [#realms] http://privacyidea.readthedocs.org/en/latest/configuration/realms.html
.. [#policies] http://privacyidea.readthedocs.org/en/latest/policies/index.html