Hi,
i am trying to setup privacyidea to be our 2FA authenticator but am having
hard time with the pam setup.
Here is our setup:
- privacyidea installed on a server it-2fa.ourdomain.de
- it-2fa runs with ubu16 xenial
- Privacyidea runs already through apache2 : https://it-2fa.ourdomain.de
- for the authentication, i have krb5 doing it and LDAP as the resolver
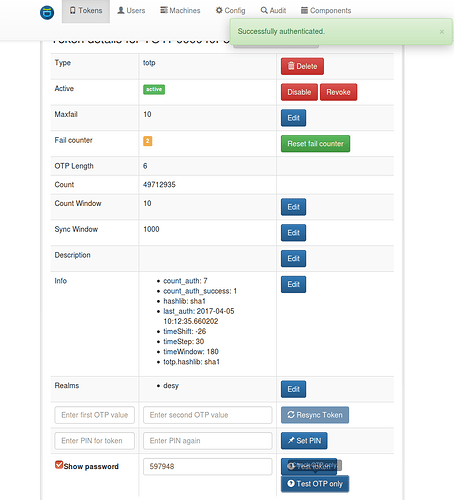
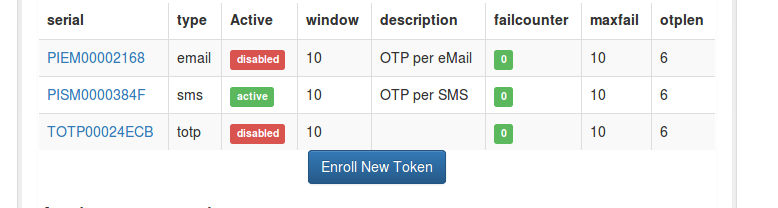
- as Example, i created a 2FA Token using a test user’s credentials
’it-user-x’ + PW which can be found in our ldap user DB. It was succesfully
authenticated against the krb5 server. - the main point to this, is setting up privacyidea to accept OTP, or U2F
or any available token for the second factor authentication after doing the
first SSH authentication using PAM.
PROBLEM:
- It seem to have a problem authenticating and i have no clue what the log
is telling me.
Apr 4 16:30:59 it-2fa sshd[13778]: pam_krb5(sshd:auth): user it-user-x
authenticated as it-user-x@OURDOMAIN.DE
Apr 4 16:30:59 it-2fa sshd: Authenticating it-user-x against
https://it-2fa.ourdomain.de
Apr 4 16:30:59 16525 sshd: requests > 1.0
Apr 4 16:30:59 it-2fa sshd: privacyidea_pam: result: {u’status’: True,
u’value’: False}
Apr 4 16:30:59 it-2fa sshd: privacyidea_pam: detail: {u’message’: u’wrong
otp pin’, u’threadid’: 140130433734400}
Apr 4 16:30:59 it-2fa sshd[13778]: Failed password for it-user-x from
131.x.x.x port 51616 ssh2
Apr 4 16:31:30 it-2fa sshd[13778]: Connection closed by 131.x.x.x port
51616 [preauth]
my common-auth pam is as follow:
auth [success=3 default=ignore] pam_krb5.so minimum_uid=1000
auth [success=2 default=ignore] pam_unix.so nullok_secure
try_first_pass
auth [success=1 default=ignore] pam_sss.so use_first_pass
here’s the fallback if no module succeeds
auth requisite pam_deny.so
prime the stack with a positive return value if there isn’t one already;
this avoids us returning an error just because nothing sets a success code
since the modules above will each just jump around
auth required pam_python.so
/lib/security/privacyidea_pam.py url=https://it-2fa.ourdomain.de
nosslverify debug
auth required pam_permit.so
Could you please help me on this??
Best Regards,
Jojo