Hello,
I’m trying to configure keycloak and privacyidea to make 2FA authentication on monitoring app (centreon)
My problem is that the login against keycloak is ok, but i can’t see anything in privacyidea log, and I never received OTP code by email.
It seems nothing is arriving to PrivacyIdea server.
The keycloak server can join the privacyidea url on 443 port, but privacyidea can’t join keycloak url on 443 port. Is this the problem?
Do I have to see something in privacyidea log when request is sent from keycloak?
I’m using Keycloak 24 and PrivacyIdea plugin KC22 (the lastest).
Regards,
Hi,
how does your flow config look in keycloak, and how is your privacyidea plugin config?
If you want to use sms, you need to trigger it beforehand.
Hello, sorry for the delay, I was out of the office.
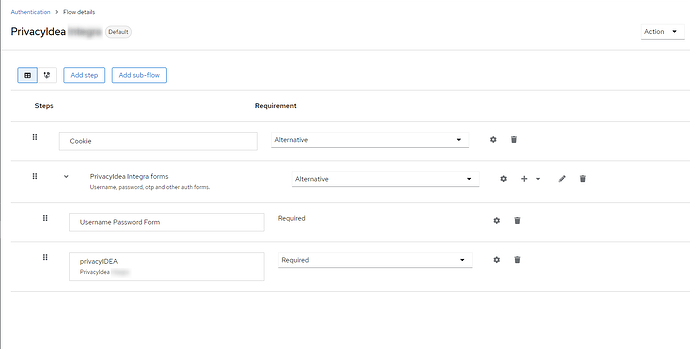
Here is authentication browser flow config:
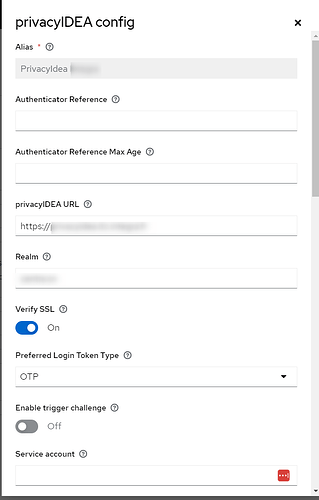
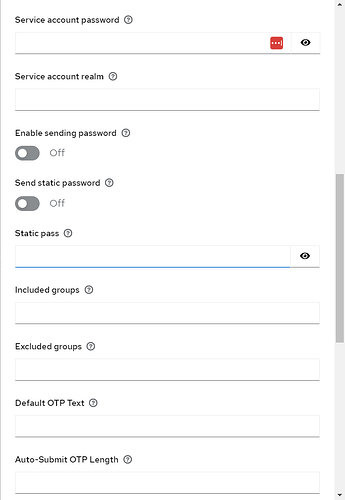
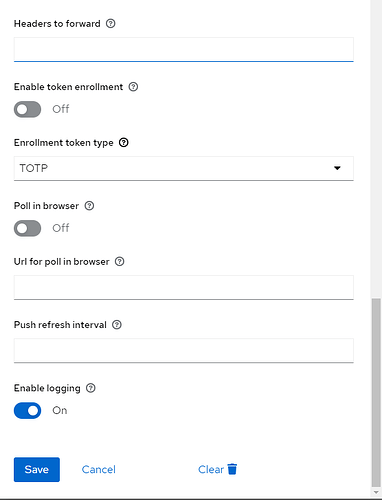
And here is the plugin config:
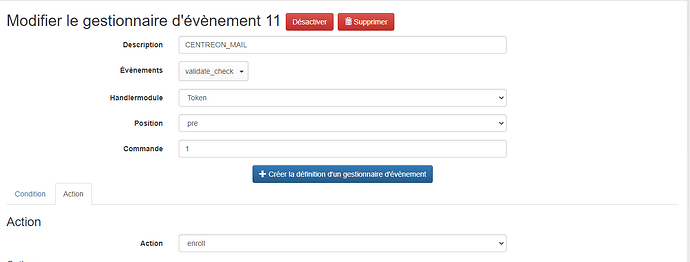
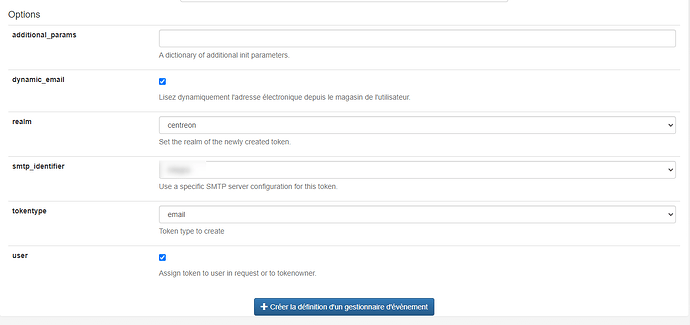
In addition, I’ve created an event in PrivacyIdea to enroll email token in pre-auth:
You need to use either triggerchallenge, send password or send static password, depending on what the pin of your sms token is.
triggerchallenge does not care about the pin because it is an admin action, but requires you to enter admin credentials in the keycloak plugin config.
send password is useful when you use the policy pin=userstore
send static password is useful when the token does not have a pin → leave the static pass empty, i.e. send an empty pass to trigger the sms
1 Like
Thanks for the quick answer.
So, my email policy uses otppin=userstore.
I enable send password then in my flow config.
I can see that in keycloak logs:
ERROR [org.privacyidea.authenticator.PrivacyIDEAAuthenticator] (OkHttp https://privacyidea.xxxx/…) PrivacyIDEA Client: : java.net.SocketException: Connection reset
Should I open 443 port from my PrivacyIdea server to my Keycloak server?
yes of course
(post must be 20 chars)
Hello,
Once again, sorry for the delay.
So, the port 443 is open between keycloak and privacyidea server.
But on keycloak I have this error:
2024-03-28 12:02:55,106 INFO [org.privacyidea.authenticator.PrivacyIDEAAuthenticator] (pool-7-thread-1) PrivacyIDEA Client: POST /validate/check
2024-03-28 12:02:55,107 INFO [org.privacyidea.authenticator.PrivacyIDEAAuthenticator] (pool-7-thread-1) PrivacyIDEA Client: user=**********
2024-03-28 12:02:55,107 INFO [org.privacyidea.authenticator.PrivacyIDEAAuthenticator] (pool-7-thread-1) PrivacyIDEA Client: pass=***************
2024-03-28 12:02:55,108 INFO [org.privacyidea.authenticator.PrivacyIDEAAuthenticator] (pool-7-thread-1) PrivacyIDEA Client: realm=centreon
2024-03-28 12:02:58,204 ERROR [org.privacyidea.authenticator.PrivacyIDEAAuthenticator] (OkHttp https://privacyidea.xxxxxx.fr/…) PrivacyIDEA Client: : java.net.SocketException: Connection reset
Did I miss something?
it seems alright for the provider itself. There is some network problem which i can not guess.
Does you privacyidea URL contain a path at the end or an ‘/’?
No, privacyidea URL doesn’t contain anything at the end.
I will continue to investigate the network.
I will post a reply if I solv the issue
Hello,
So, we managed to make network works. The request reach PrivacyIdea server, but it fails to authenticate against the Active Directory.
It’s weird because when we test the user in privacyidea it’s Ok.
The password send by the keycloak privacy plugin seems wrong. Do you know if it’s possible to see the password in keycloak log in clear text to check that?
Regards,
Hi, it is not possible with the official jar. However, the amout of * 's is equal to the length of the password if that is helpful. Also if you get past the first step in keycloak, it should be already verified and correct.
If you want to see the password in cleartext, you would need to rebuild the java-client and then the keycloak plugin.
Ok, I’ve decided to use empty static password, so PrivacyIdea doesn’t have to authenticate against Active Directory, only Keycloak did.
It’s working perfectly.
Thanks for your time