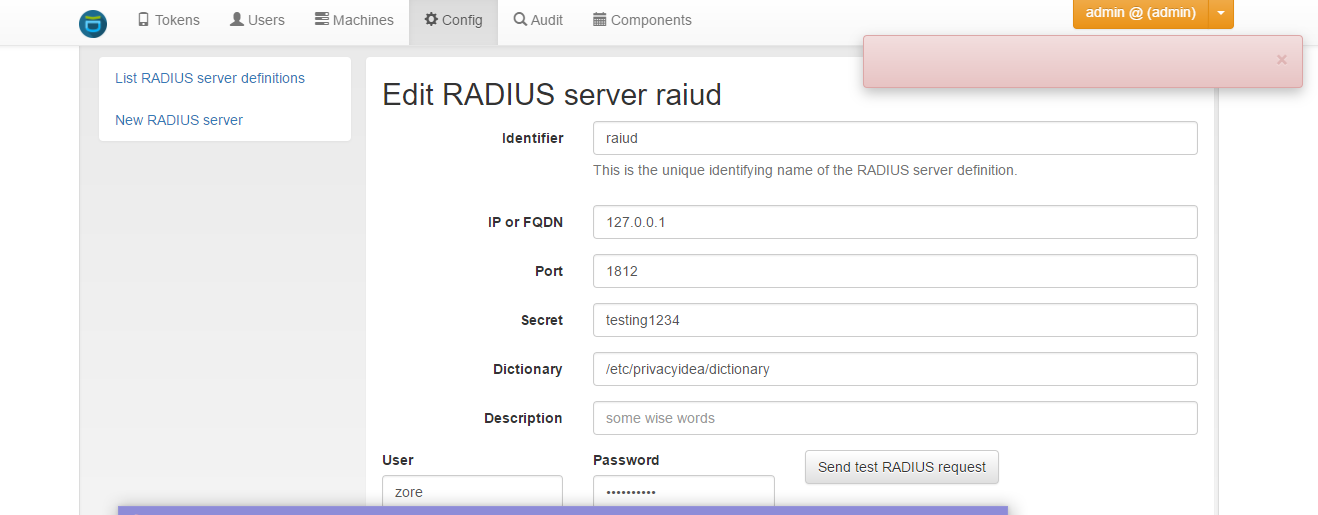
I have run privacyidea server and freeradius server on ubunutu14.04 by deb pkg.
But now i use freeradius for my ssh user pasword certification,it work .
but when i use it with privacyidea server there Some have problems whit it when i open new xshell and try to login user in /etc/passwd without input pasword the radius -X show me like this more then two time .
rad_recv: Access-Request packet from host 127.0.0.1 port 23695, id=41, length=88
User-Name = "zore"
User-Password = "M\333\366\371^/\251z*\020¹X\306O\""
NAS-IP-Address = 127.0.1.1
NAS-Identifier = "sshd"
NAS-Port = 22670
NAS-Port-Type = Virtual
Service-Type = Authenticate-Only
Calling-Station-Id = "192.168.90.1"
# Executing section authorize from file /etc/freeradius/sites-enabled/privacyidea
+- entering group authorize {...}
++[preprocess] returns ok
++[digest] returns noop
[suffix] No '@' in User-Name = "zore", looking up realm NULL
[suffix] No such realm "NULL"
++[suffix] returns noop
[ntdomain] No '\' in User-Name = "zore", looking up realm NULL
[ntdomain] No such realm "NULL"
++[ntdomain] returns noop
[files] users: Matched entry DEFAULT at line 1
++[files] returns ok
++[expiration] returns noop
++[logintime] returns noop
[pap] WARNING! No "known good" password found for the user. Authentication may fail because of this.
++[pap] returns noop
Found Auth-Type = Perl
# Executing group from file /etc/freeradius/sites-enabled/privacyidea
+- entering group Perl {...}
rlm_perl: Config File /etc/privacyidea/rlm_perl.ini found!
rlm_perl: Debugging config:
rlm_perl: Default URL https://localhost/validate/check
rlm_perl: Looking for config for auth-type Perl
rlm_perl: Auth-Type: Perl
rlm_perl: url: https://localhost/validate/check
rlm_perl: user sent to privacyidea: zore
rlm_perl: realm sent to privacyidea:
rlm_perl: resolver sent to privacyidea:
rlm_perl: client sent to privacyidea: 127.0.1.1
rlm_perl: state sent to privacyidea:
rlm_perl: urlparam pass
rlm_perl: urlparam user
rlm_perl: urlparam client
rlm_perl: Not verifying SSL certificate!
rlm_perl: privacyIDEA request failed: 500 INTERNAL SERVER ERROR
rlm_perl: privacyIDEA Result status is false!
rlm_perl: privacyIDEA access denied
rlm_perl: return RLM_MODULE_REJECT
rlm_perl: Added pair User-Password = M\333\366\371^/\251z*\020¹X\306O\"
rlm_perl: Added pair NAS-Port-Type = Virtual
rlm_perl: Added pair NAS-Port = 22670
rlm_perl: Added pair NAS-Identifier = sshd
rlm_perl: Added pair NAS-IP-Address = 127.0.1.1
rlm_perl: Added pair Service-Type = Authenticate-Only
rlm_perl: Added pair Calling-Station-Id = 192.168.90.1
rlm_perl: Added pair User-Name = zore
rlm_perl: Added pair Reply-Message = 'ascii' codec can't encode character u'\xb9' in position 25: ordinal not in range(128)
rlm_perl: Added pair Auth-Type = Perl
++[perl] returns reject
Failed to authenticate the user.
Delaying reject of request 154 for 1 seconds
Going to the next request
Waking up in 0.8 seconds.
Sending delayed reject for request 154
Sending Access-Reject of id 41 to 127.0.0.1 port 23695
Reply-Message = "'ascii' codec can't encode character u'\\xb9' in position 25: ordinal not in range(128)"
Waking up in 4.9 seconds.
here is the log of auth.log
Jun 10 19:30:56 ubuntu sshd[22673]: PAM _pam_load_conf_file: unable to open /etc/pam.d/password-auth
Jun 10 19:30:56 ubuntu sshd[22673]: PAM unable to dlopen(pam_winbind.so): /lib/security/pam_winbind.so: cannot open shared object file: No such file or directory
Jun 10 19:30:56 ubuntu sshd[22673]: PAM adding faulty module: pam_winbind.so
Jun 10 19:30:56 ubuntu sshd[22673]: pam_radius_auth: DEBUG: getservbyname(radius, udp) returned 515816512.
Jun 10 19:30:57 ubuntu sshd[22673]: pam_radius_auth: packet from RADIUS server 127.0.0.1 fails verification: The shared secret is probably incorrect.
Jun 10 19:30:57 ubuntu sshd[22673]: pam_radius_auth: DEBUG: getservbyname(radius, udp) returned 515816512.
Jun 10 19:30:58 ubuntu sshd[22673]: pam_radius_auth: RADIUS server 127.0.0.1 failed to respond
Jun 10 19:30:58 ubuntu sshd[22673]: pam_radius_auth: DEBUG: get_ipaddr(other-server) returned 0.
Jun 10 19:30:58 ubuntu sshd[22673]: pam_radius_auth: Failed looking up IP address for RADIUS server other-server (errcode=9)
Jun 10 19:30:58 ubuntu sshd[22673]: pam_radius_auth: All RADIUS servers failed to respond.
Jun 10 19:30:58 ubuntu sshd[22673]: pam_radius_auth: DEBUG: getservbyname(radius, udp) returned 515816512.
Jun 10 19:30:59 ubuntu sshd[22673]: pam_radius_auth: RADIUS server 127.0.0.1 failed to respond
Jun 10 19:30:59 ubuntu sshd[22673]: pam_radius_auth: DEBUG: getservbyname(radius, udp) returned 515816512.
Jun 10 19:30:59 ubuntu sshd[22673]: pam_radius_auth: packet from RADIUS server 127.0.0.1 fails verification: The shared secret is probably incorrect.
Jun 10 19:31:00 ubuntu sshd[22673]: pam_radius_auth: DEBUG: get_ipaddr(other-server) returned 0.
Jun 10 19:31:00 ubuntu sshd[22673]: pam_radius_auth: Failed looking up IP address for RADIUS server other-server (errcode=9)
Jun 10 19:31:00 ubuntu sshd[22673]: pam_radius_auth: All RADIUS servers failed to respond.
Jun 10 19:31:00 ubuntu sshd[22673]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=192.168.90.1 user=zore
Jun 10 19:31:04 ubuntu sshd[22673]: error: Received disconnect from 192.168.90.1: 0: [preauth]
And when i input the PIN+OTP this maybe let more than five time to succeed
login and i find i can’t use the password in /etc/passwd to login
my conf file like this
THE /etc/pam_radius.conf
127.0.0.1 testing123 1
THE /etc/pam.d/sshd
auth sufficient /lib/security/pam_radius_auth.so
auth include password-auth
@include otp-auth
#...... more default
THE /etc/pam.d/otp-auth
auth [success=3 default=ignore] pam_radius_auth.so
auth [success=2 default=ignore] pam_unix.so nullok_secure try_first_pass
auth [success=1 default=ignore] pam_winbind.so krb5_auth krb5_ccache_type=FILE cached_login try_first_pass
# here's the fallback if no module succeeds
auth requisite pam_deny.so
# prime the stack with a positive return value if there isn't one already;
# this avoids us returning an error just because nothing sets a success code
# since the modules above will each just jump around
auth required pam_permit.so
# and here are more per-package modules (the "Additional" block)
auth optional pam_ecryptfs.so unwrap
auth optional pam_cap.so
I have find more it in wiki and google but it Still nothing help .
So can you get me some help ?
With kind regards
Zore