Hello,
I have installed a privacyIDEA ver 3.0.2 on a CentOS7 machine.
And, I have another two client machines one is CentOS7 and one is Ubuntu18.
Then, I have created a HOTP token and assign to both two client machines.
I also trying PIN and Token of this HOTP token on the privacyIDEA admin web portal and everything are okay.
But, when I try to set my client machines I want to use the 2FA authentication when I SSH login to.
Like the way Google-authentication PAM.
But, I don’t know how to set that.
I also searching for many online documents and examples on the internet for this but no answer for this.
And many documents are talking about the FreeRadius with the privacyIDEA.
So, I would like to hope someone can help me with the below question:
If I hope every time I use SSH way to log in to some servers and must pass the 2FA via privacyIDEA no matter HOTP or Email or SMSS which one, How I can success has done these settings.
Please, I hope has some clear SOP or documents can help me.
Thank you.
Hello Chi Chen,
welcome to the privacyIDEA community and thank you for looking at privacyIDEA.
You want to login via SSH by authenticating with an HOTP token against privacyIDEA?
You can do this. You SSH server has to communitcate with privacyIDEA. There is no need to assign a token to a machine in this case.
The SSH server will probably use the PAM stack to communicate via the RADIUS protocol to privacyIDEA. In this case you would need to use pam_radius on the “client machine” - a.k.a. the SSH server and you need to use FreeRADIUS with the privacyidea freeradius plugin on the privacyIDEA server.
I hope this top level view helps to understand, how pieces work togeather.
Regards
Cornelius
Hi, Cornelius,
Yes, I think I can know you said.
But, please allow me for confirming below things:
First, in my case I have to set two servers for 2FA SSH login to my client machines., One is privacyIDEA server and one is SSH server.
Thus,
SSH server has to install the FreeRadius package and enable FreeRadius services, is correct?
All my client machines have to change or modify “/etc/pam.d/sshd” content to using pam_radius?
About the…
" a.k.a. the SSH server and you need to use FreeRADIUS with the privacyidea freeradius plugin on the privacyIDEA server."
It means, privacyIDEA server also have to install FreeRADIUS and enable FreeRADIUS services?
Thank you for your helping.
Regards,
Cain Chen
Hello Cain Chen,
privacyIDEA Server
Here you install:
- privacyIDEA
- FreeRADIUS (it is the FreeRADIUS Server)
- privacyIDEA FreeRADIUS plugin.
Now privacyIDEA can answer RADIUS requests.
SSH Server
Here you install
- pam_freeradius
- and configure this as a freeradius client to the FreeRADIUS server on the privacyIDEA machine.
Client Machines
Here you install nothing: No RADIUS, no privacyIDEA.
You do not need to configure anything!
When authenticating to the SSh server the users get one or more password prompts (depending on your PAM config on the SSH server) where they enter either passwords or OTP (depending on your PAM config on the SSH server)
Hi Cornelinux,
I will try it.
I think I have many ideas in privacyIDEA to strong my server site and client security,
Thanks a lot!
Cain
Hello,
I followed the online document but got frustrating results.
I followed below link for installing privacyIDEA server and FreeRADIUS server
Below are my situation:
- Client (a CentOS7 on the VirtualBox)
- privacyIDEA server and FreeRADIUS server (a CentOS7 on the VirtualBox)
About the FreeRADIUS server on the privacyIDEA server, I am used following command for installation:
yum install freeradius freeradius-utils
About the privacyIDEA FreeRADIUS plugin I am download from:
https://raw.githubusercontent.com/privacyidea/FreeRADIUS/master/privacyidea_radius.pm - SSH server (a CentOS7 on the VirtualBox)
I install pam_freeradius use command:
yum install pam_radius
FreeRADIUS client setting on the SSH server:
— /etc/raddb/server —
server_ip testing123 20
— End —
— /etc/pam.d/sshd —
#%PAM-1.0
auth sufficient pam_radius_auth.so
…
— End —
But, I still get failed result when my client ssh login to SSH server.
And, my client login to SSH server via SSH key authentication, not the password.
I hope can use SSH key + HOTP for my ssh authentication
I have successfully use SSH key + Google-authentication(Installed on SSH server).
But, I am looking for the privacyIDEA because I want to use more token look like Email and SMS.
But, the SSH key + HOTP this so easy way I stilling can’t successfully use by privacyIDEA.
If I choose SSH key + HOTP does it mean that I don’t need any FreeRADIUS package whether privacyIDEA or SSH server or client machine?
And, what is the “privacyidea-pam” module and which token type we will choose for it?
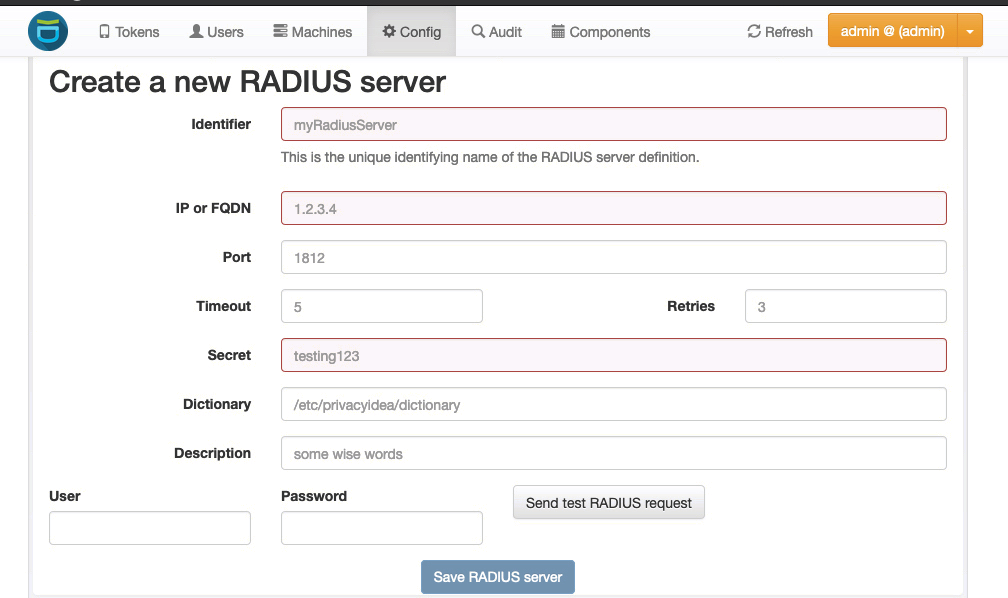
By the way, do I need to add a FreeRADIS server to the config of the privacyIDEA admin portal?
Regards,
Cain
Hello Cain,
This is a complicated setup and you expect to plug everything togeather and work right from the start?
How long have you been working with computers?
Do you have any experience how to approach a not familiar territory?
You must not do everything at once. Go one step after the other.
Check if step one works. And then only proceed to step 2.
You have a setup with 5 different componts. How should I know why this does not work, as you do not provide any information?
Please do yourself a favour and use the google auth module.
I am very sorry for the harsh words, but this obviously does not make any sense here. You are dropping tons of random questions and do not tell, where you fail. Probably you have not figured it out. You need to approach IT challenges in a more analytic way!
- Check if you can authenticate against privacyIDEA via REST protocol
- Setup the RADIUS server
- Check if you can authenticate via the RADIUS protocol
- Configure your SSH server as the RADIUS client in the Radius clients.conf
- check if you can authenticate via the RADIUS protocol from the SSH server.
- ONLY AFTER THIS WORKS, SET UP YOUR SSH Server!!!
- Check in the auth log (I do not know by heart which it is on CentOS to see what happens in the PAM stack) hint: setup a pam config and test with a local “login”.
hint #2: Read a lot about PAM.
By the way: If you have a trusted ssh key it will always use this SSH key!
If you want to do both, use this in you sshd config:
AuthenticationMethods publickey,password
Regards
Cornelius