Hello,
I want to use privacyIdea as SSH keys manager for our Linux VMs. The problem is, when I’m looking for create a low admin rights account for the token fetch I add a policy and each time the rights of my admins accounts are “disabled”. Can someone give me a step-by-step tutorial to create a low rights admin please?
An example of a policy:
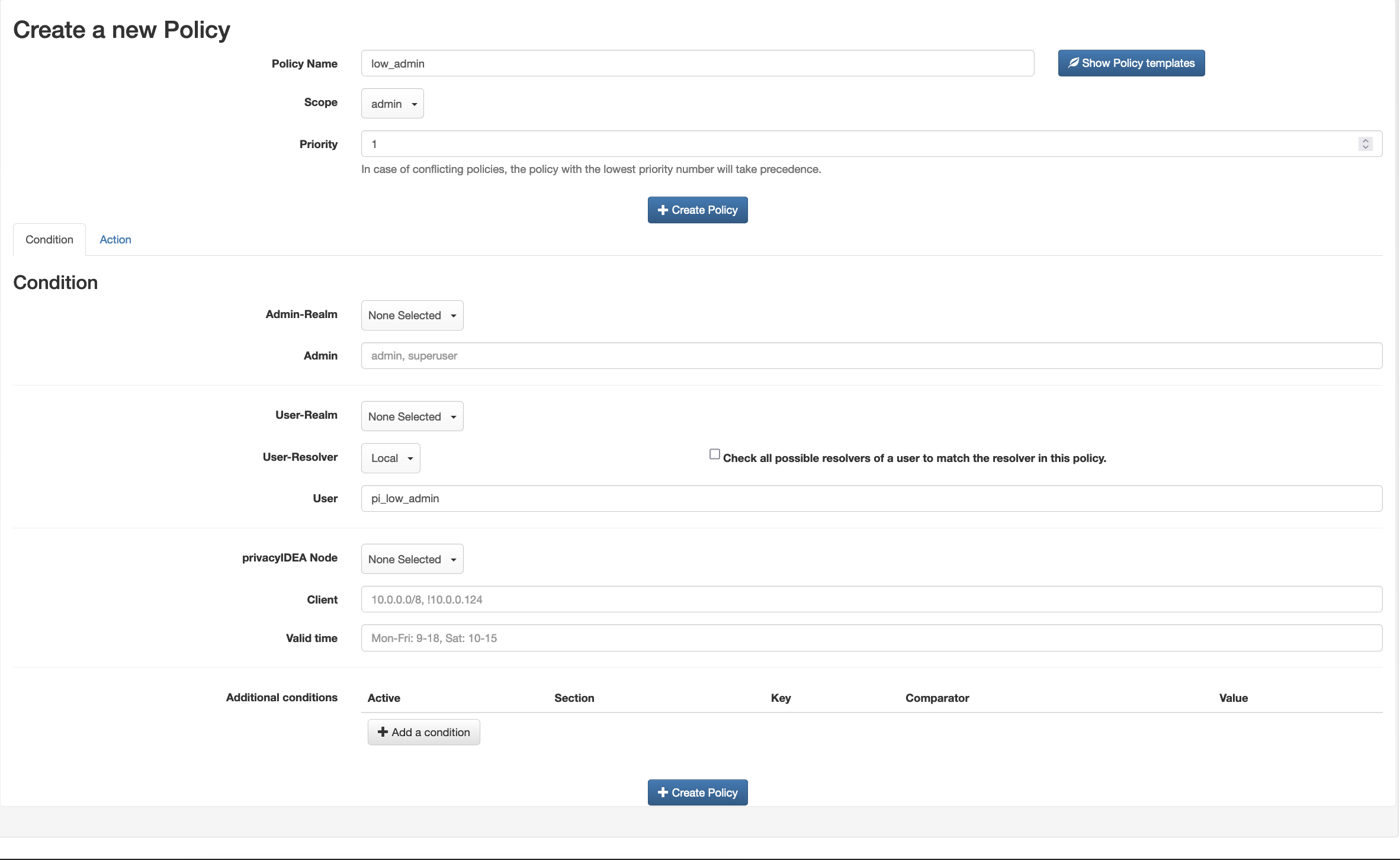
Thanks,
Regards.
Hello,
this is a common error. Please read the first note here:
https://privacyidea.readthedocs.io/en/latest/policies/admin.html
As long as you have no admin policies, every administrator is allowed to do everything. Once you set the first admin policy, it is checked and restricts the permissions for all your admins.
- create an admin policy for your current admin to grant administration rights (use template for instance)
- create lower privileged policy for your helpdesk-type admins
Best regards,
Henning
Hello,
Thanks for your answer.
When I create the superuser policy with “super” in “Admin-Realm” my local default admin (created in shell) don’t have not longer admin rights, is it normal?
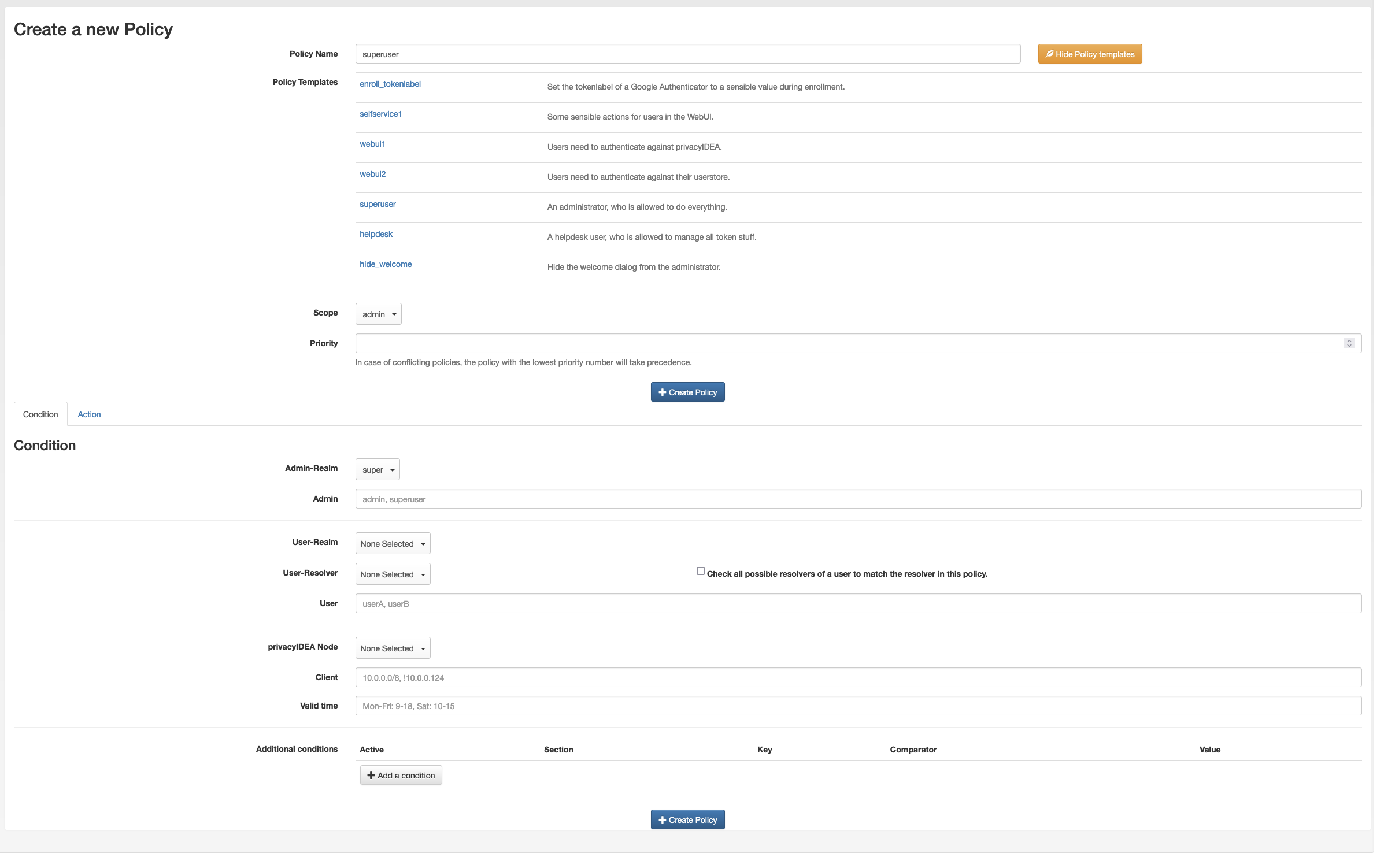
Best.
Hello,
Is somebody has an idea please? I’m sure I don’t understand something 
Actually I have one local privacy idea admin and my Active Directory users (one group of them are admin and other just users)
Best.
Read the docs.
https://privacyidea.readthedocs.io/en/latest/faq/admins.html
“super” is an example - or did you create an admin-realm, that is called super?
You local admin is not contained in any realm!
“super” is an example.
I want to create an account who can just fetch tokens but each time I create an “admin” scope policy, all superusers are affected.
Read the documentation carefully!
Your policy will effect all admins if you leave the admin users empty.
This is how policies always work. If you do not define a condition, the policy will match for every scenario.
No admin user defined => policy matches for all admins.
And please see laclaros comment!!! !!


