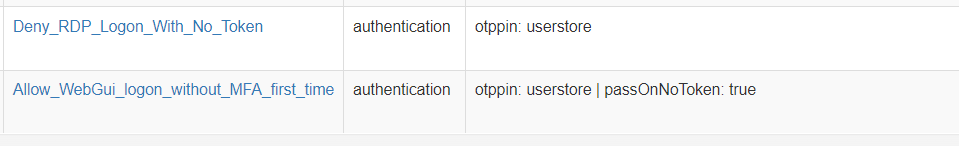
I use passOnNoToken and TokenWizard to allow users to authenticate without MFA to WebGui for the first time. I’d like to restrict this behavior to the WebGui only but passOnNoToken allows any authentication to pass. I want to restrict RDP users authenticating to PI without MFA but I don’t see a condition that filters for users who don’t have a token. I’ve tried token count < 1 but if they have no token this condition throws an undefined error when evaluated.
Deny_RDP_Logon_With_No_Token should only apply to users with no active token or users authenticating from RDP (if there was a way to detect that)
Well passthru: userstore should be used instead of passOnNoToken but the issue still remains.
Do I get it right? You only want the user to login to the webui intially, not to any other service connected to the privacyIDEA system?
This is correct and I found a way that works but maybe there is a better way. I was able to target a policy at RDP by adding a condition of ‘User-Agent’ http request header and matching on ‘privacyidea-cp’ which is the user-agent name of the PI Credential Provider for RDP. I could probably also match on the ‘X-Forwarded-For’ key which would have the ip of the RDP server. I could not find a way to filter users who had no active tokens but looks like that is not needed.
You could add the client condition to the passthru policy.
This way you can control, that it will only match from arbitrary clients. You can exclude the IP of the RDP server. Thus user would only able to e.g. rollout from their own desktop but require the 2nd factor for log in to the terminal server.
However, defining the rollout process is an individual detailed task.