I want to use Active Directory users for authentication and it worked with me but I couldn’t configure the authentication to be work per Active Directory Group
Now all Active Directory Groups can connect to FortiGate using ssl-vpn but I want to specify only some groups to be authenticated groups
rule all users can connect, and it work with no errors
but when try to configure policy to specific domain group it didn’t work and it gives me the permission is denied
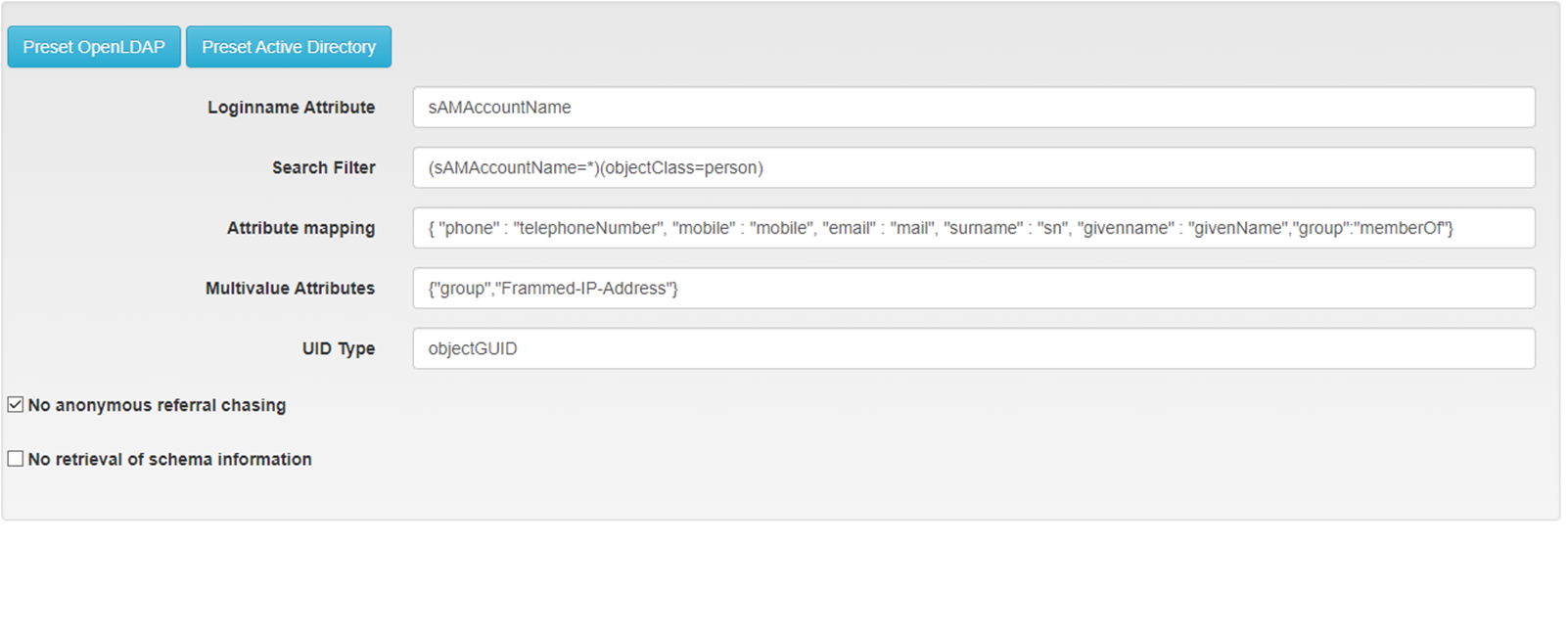
Privacyidea Configuration
Path=== /etc/privacyidea/rlm_perl.ini
[Attribute Filter-Id]
dir = user
userAttribute = group
regex = CN=Test-otp, OU=VPN-Users,DC=AD,DC=com
Freeradius Logs
Tue Nov 30 14:46:36 2021 : Info: rlm_perl: Config File /etc/privacyidea/rlm_perl.ini found!
Tue Nov 30 14:46:36 2021 : Info: rlm_perl: Debugging config:
Tue Nov 30 14:46:36 2021 : Info: rlm_perl: Default URL ttps://localhost/validate/check
Tue Nov 30 14:46:36 2021 : Info: rlm_perl: Looking for config for auth-type Perl
Tue Nov 30 14:46:36 2021 : Info: rlm_perl: Setting client IP to 10.10.10.10.
Tue Nov 30 14:46:36 2021 : Info: rlm_perl: Auth-Type: Perl
Tue Nov 30 14:46:36 2021 : Info: rlm_perl: url: https://localhost/validate/check
Tue Nov 30 14:46:36 2021 : Info: rlm_perl: user sent to privacyidea: otp2
Tue Nov 30 14:46:36 2021 : Info: rlm_perl: realm sent to privacyidea:
Tue Nov 30 14:46:36 2021 : Info: rlm_perl: resolver sent to privacyidea:
Tue Nov 30 14:46:36 2021 : Info: rlm_perl: client sent to privacyidea: 10.10.10.10
Tue Nov 30 14:46:36 2021 : Info: rlm_perl: state sent to privacyidea: 5642131642123132
Tue Nov 30 14:46:36 2021 : Info: rlm_perl: urlparam pass
Tue Nov 30 14:46:36 2021 : Info: rlm_perl: urlparam state
Tue Nov 30 14:46:36 2021 : Info: rlm_perl: urlparam client
Tue Nov 30 14:46:36 2021 : Info: rlm_perl: urlparam user
Tue Nov 30 14:46:36 2021 : Info: rlm_perl: Request timeout: 10
Tue Nov 30 14:46:36 2021 : Info: rlm_perl: Not verifying SSL certificate!
Tue Nov 30 14:46:36 2021 : Info: rlm_perl: elapsed time for privacyidea call: 0.132376
Tue Nov 30 14:46:36 2021 : Info: rlm_perl: privacyIDEA access granted
Tue Nov 30 14:46:36 2021 : Info: rlm_perl: ++++ Parsing group: Attribute
Tue Nov 30 14:46:36 2021 : Info: rlm_perl: +++++ Found member ‘Attribute Filter-Id’
Tue Nov 30 14:46:36 2021 : Info: rlm_perl: ++++++ Attribute: IF ‘user’->‘group’ == CN=Test-otp, OU=VPN-Users,DC=AD,DC=com’ THEN ‘Filter-Id’
Tue Nov 30 14:46:36 2021 : Info: rlm_perl: ++++++ searching in directory user
Tue Nov 30 14:46:36 2021 : Info: rlm_perl: +++++++ User attribute is a list: ARRAY(ZxYYYYYY)
Tue Nov 30 14:46:36 2021 : Info: rlm_perl: +++++++ trying to match CN=Test-otp, OU=VPN-Users,DC=AD,DC=com
Tue Nov 30 14:46:36 2021 : Info: rlm_perl: ++++++++ Result: Add RADIUS attribute Filter-Id =
Tue Nov 30 14:46:36 2021 : Info: rlm_perl: return RLM_MODULE_OK
privacyidea log
[2021-11-30 14:46:36,267][2161][140709409437440][INFO][privacyidea.lib.resolvers.LDAPIdResolver:322] Setting system wide POOLING_LOOP_TIMEOUT to 10.
[2021-11-30 14:46:36,268][2161][140709409437440][INFO][privacyidea.lib.user:237] user ‘otp2’ found in resolver ‘AD.com’
[2021-11-30 14:46:36,268][2161][140709409437440][INFO][privacyidea.lib.user:238] userid resolved to ‘XXXXXXXX-YYYY-ZZZZ-XXXX-YYYYYYYYYYYY’
[2021-11-30 14:46:36,337][2161][140709409437440][INFO][privacyidea.api.lib.postpolicy:471] There is no machine with IP=IPAddress(‘127.0.0.1’)