Hi folks,
i’m new to privacyidea, we just set it up for Fortigate VPN Login with OTP. Users are authenticated via ldap resolvers, one resolver for each ldap user group. It works in general, but our VPN-Policies for SSL-VPN contain the user group. For example: member of Admin-Group = Admin-Policy, member of User-Group = User-Policy.
Is it possible to return the ldap user group in the radius reply, so the Fortigate can match users to policies?
I found some options in authorisation policy template, like “add_resolver_in_response” or “add_user_in_response”, but that doesn’t seem to work :-/
Any suggestions are welcome!
Kind regards
Theo
A couple things need to be setup…
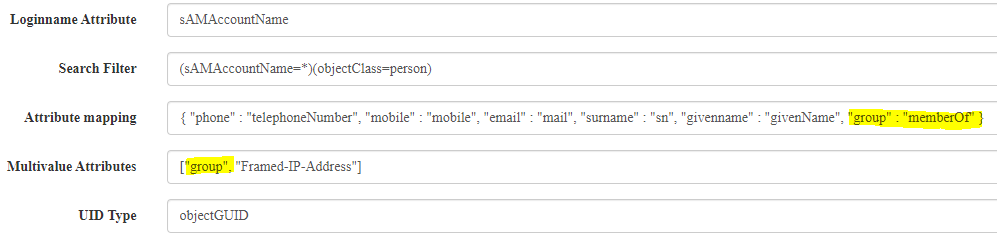
Configure your user resolver to pull and map attributes from your user store into PrivacyIDEA. So, assuming you want to pull user store attribute memberOf and map it to `group in PrivacyIDEA, your resolver should look something like below. You’ll also need to put the attribute name in the Multivalue attributes section.
Then, you need to configure your rlm_perl.ini file to return the group(s) in the Fortinet VSA. The value inside the regular expression capture group is what is sent in the RADIUS response
[Attribute Fortinet-Group-Name]
dir = user
userAttribute = group
regex = CN=(SpecialGroup).*
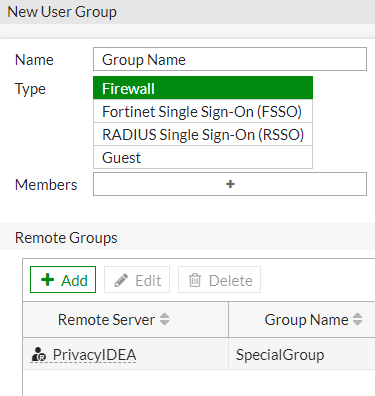
Finally on the Fortigate, configure a firewall user group, select the RADIUS server, and then enter a group name that will be returned in the RADIUS response.
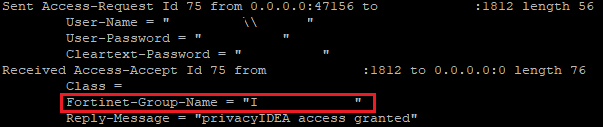
You can test this with radclient. The user-password in the command below depends on your setup. The auth password at the end is whatever the password you setup for the machine you are running the test from in your clients.conf file.
echo 'User-Name=REALM\\USERNAME, User-Password=PIN+OTP' | radclient -x SERVERFQDN auth SECRET
Reference: FreeRADIUS/rlm_perl.ini at master · privacyidea/FreeRADIUS · GitHub (Attribute Filter-Id)
1 Like
Hi,
thanks for your advice. After some playing around with radius attributes and group names it finally works!
[Attribute Fortinet-Group-Name]
dir = user
userAttribute = group
regex = CN=VPN-(.*),CN=Users,DC=######,DC=###
hi
how it is work with you
i can not apply diffrent access for radius groups


