i have configured validity time for Email OTP token to be 1 min , and i have tried to use this OTP after its validity time , actually i tried it after 4 hours and it works .
is there anything wrong i have done ?
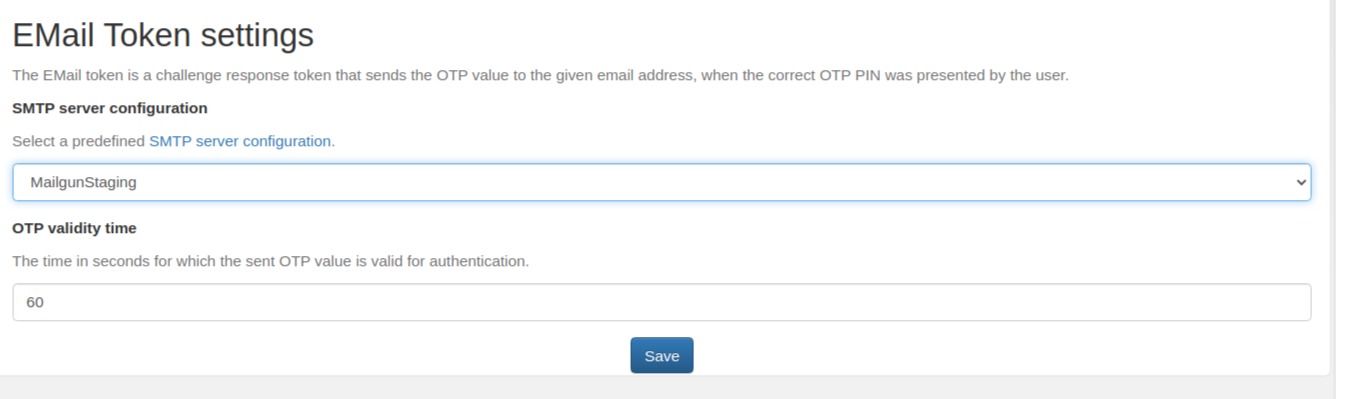
i have configured validity time for Email OTP token to be 1 min , and i have tried to use this OTP after its validity time , actually i tried it after 4 hours and it works .
is there anything wrong i have done ?

privacyIDEA 3.4.1
i’m doing trigger challenge
This sounds like a known side effect.
You can either
ok , but i’m little confused about OTP PIN , as i’m using keycloak for authentication and privacyidea for 2FA with trigger challenge an email OTP
can you guide me ?
Hi,
I am also facing same problem. I am using PI version 3.5 and using trigger challenge without OTP PIN.
I have set OTP validity time to 60 (seconds) but email OTP never expires, it is validating it even after 60 seconds.
Did anyone identify an answer to this issue?
I am new to privacyIDEA and I just set up locally with default config (from master branch) and I am facing same issue as well.
I configured following
Am I doing something wrong in this flow?
This is a misunderstanding of the validity of an SMS or Email OTP value.
Teh email/SMS token is based on HOTP. That means from a mathematical standpoint a given value is valid until it is being used. No matter if it is one minute or two years.
The validity of 60 seconds you mention is the validity of the challenge. The SMS and Email being challenge response token means:
However, if a user chooses to authenticate without a transcation_id but with the PIN+OTP value, this authentication will work, outside of the challenge-response logic with the 60-second-limit
Now you might be able to deduce what obviously happens in some special cases like if you do not have an OTP PIN ![]()
I think, I at least got one part working. Thanks @cornelinux for your help!
I tried hitting this endpoint for trigger challenge flow. This triggered an email to the user with OTP value in it and returns transaction_id as well in the response.
curl --location --request POST ‘http://127.0.0.1:5000/validate/triggerchallenge?user=sagar@gmail.com&serial=PIEM0027174A&realm=ycu’
–header 'PI-Authorization: ’
As a next step, I went on to validate that user entering this correct OTP but after the expiry time (60 seconds).
curl --location --request GET ‘http://127.0.0.1:5000/validate/check’
–header ‘Content-Type: application/x-www-form-urlencoded’
–data-urlencode ‘pass=193876’
–data-urlencode ‘transaction_id=05868362562103843367’
–data-urlencode ‘user=sagar@gmail.com’
So I am calling this endpoint with correct OTP, but after 1 minute.
And this endpoint returns the following error in both scenarios.
Error message: “Response did not match the challenge”
Scenario 1: When incorrect OTP is passed and
Scenario 2: When challenge flow has expired.
Is there a way to know whether failure happened because OTP was incorrect or was it expired?
omit otponly. This breaks your challenge response!
Coincidence that I was updating the thread with my working solution and you responded with clarification on otponly around same time. ![]()
So for now my only question is on this.
I see same error message: “Response did not match the challenge” in following two scenarios. Is there a way to find what was the root cause from these two?
Scenario 1: When incorrect OTP is passed and
Scenario 2: When challenge flow has expired.
Who would want to know this and why?
Who would want to know this and why?
This is just to let the user know whether the failure is caused because of the OTP got expired or it just is invalid.
I am facing the issue regarding user cache.
I have enabled the user cache by configuring expiration timeout (540 seconds). Still UserIdResolver (http resolver) is hitting the server (to fetch user’s email/phone data) multiple times within the expiration timeout period.
Is am missing some steps/configuration?
welcome to privacyIDEA, @shubham_upadhyay
But only it is “time”, you are totally posting in the wrong topic!
There is a chapter about user cache in the docs.
Only the userid/resolver is cached. No user attributes are cached. So works as designed.